We're an Embedded Award 2026 Tools nominee and would love your support! Vote for C/C++test CT >>

CWE
CWE (Common Weakness Enumeration) is a comprehensive list of over 800 programming errors, design errors, and architecture errors that may lead to exploitable vulnerabilities — more than just the Top 25. The CWE/SANS Top 25 Most Dangerous Software Errors is a shortened list of the most widespread and critical errors that may lead to serious vulnerabilities in software, that are often easy to find and exploit. These are the most dangerous weaknesses because they enable attackers to completely take over the software, steal software data and information, or prevent the software from working at all.
Parasoft is certified as CWE Compatible, which means that Parasoft users can easily understand which static analysis checker is associated with which CWE during configuration, remediation, and reporting. Because of Parasoft’s CWE-centric approach, you don’t actually have to do anything special — just fix the violations and automatically generate what you need for compliance. Parasoft has also assisted prioritization (triage) and audit (suppress) activities by incorporating the CWE technical impact into the analytics hub.
As shown to the right, Parasoft’s unique real time feedback gives users a continuous view of compliance with the CWE, by providing interactive compliance dashboards, widgets, and reports that have the CWE risk assessment framework implemented right within the dashboard itself.
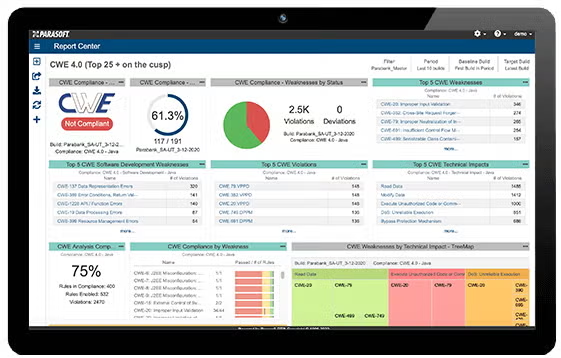
Parasoft users can leverage Parasoft’s static code analysis products for C/C++, Java, and .NET to reduce the cost of achieving CWE compliance and save time and effort.
Parasoft supports CWE guidelines with dedicated code analysis configurations that map to best practices outlined in the standard. Parasoft supports MITRE’s Common Weakness Enumeration (CWE) for C, C++, Java, and .NET languages.
Parasoft’s policy-driven approach defines the organization’s expectations around quality while ensuring consistent, unobtrusive policy application. The automated infrastructure automatically monitors policy compliance for visibility and auditability.
Parasoft’s out-of-the-box CWE mappings mean that users don’t have to waste time trying to figure out what checkers are for which CWEs when configuring, and when fixing, users will always inherently know which CWE is being worked on because the static analysis checker names tell you.
For auditing and reports, Parasoft shows exactly which rules are covered by each checker, including a full set of PDF files showing compliance plan and deviation reports — but you almost don’t need the compliance plan, because the names are the same as CWE.

WHITEPAPER
Learn more about how to achieve software security with a rigorous standards-based development process.
