Take a faster, smarter path to AI-driven C/C++ test automation. Discover how >>
News
March 30, 2020
Parasoft continues to lead in enforcement of the most current ruleset of the MISRA C:2012 standard
Monrovia, CA – Parasoft, a global software testing automation leader for over 30 years, announces its support of the newly released MISRA C:2012 Amendment 2, which incorporates the support of the C language standard ISO/IEC 9899:2011, commonly referred to as C11. C11 replaces C99 (standard ISO/IEC 9899:1999) and has been superseded by C18 (standard ISO/IEC 9899:2018). In addition, the MISRA C Working Group released the MISRA Compliance 2020 guidelines, which are now mandatory to claim compliance with the standard. The Parasoft suite guides users through the process of building the Guidelines Enforcement Plan (GEP) and Guidelines Recategorization Plan (GRP) and automatically generate Guidelines Compliance Summary (GCS) together with a full list of approved deviations.
To read more about Parasoft’s support of MISRA C:2012 Amendment 2 visit our blog: https://www.parasoft.com/blog/misra-c-c-code-checking//
"The C11 and C18 Standards are now widely adopted in the industry and replace outdated C99. MISRA C2012 Amendment 2 provides initial guidelines to restrict and limit the usage of the new language constructs that may be unsafe and insecure," said Miroslaw Zielinski. "Subsequent amendments are expected to lift these restrictions and provide more specific guidelines for the extensions introduced in C11/C18. Parasoft static analysis tools already support MISRA C2012 Amendment 2 and will support the future updates of the MISRA C2012 standard as they become available."
The MISRA C and C++ working groups, of which Parasoft is a member, continues to provide guidance in reducing or removing coding defects and avoiding unpredictable behavior while enabling safety and security. In the MISRA C2012 Amendment 2, users will find new rules that apply to the standard library, where functions have been identified and shall not be used due to security vulnerabilities introduced. Given that the C language is prone to an enormous family of buffer overflow vulnerabilities, it’s critical that the organizations that build embedded safety-and security-critical systems are analyzed for security weaknesses.
Other C11 and C18 code behaviors have been identified as having occurrences of undefined or unspecified actions. Some language features, though well defined, do not meet developer expectations. During code analysis, these code constructs will be tagged with a violation, and any use of the language feature must be measured and supported by a deviation. In the end, the MISRA working group has taken the opportunity to make updates to the standard, lifting it to a whole new benchmark.
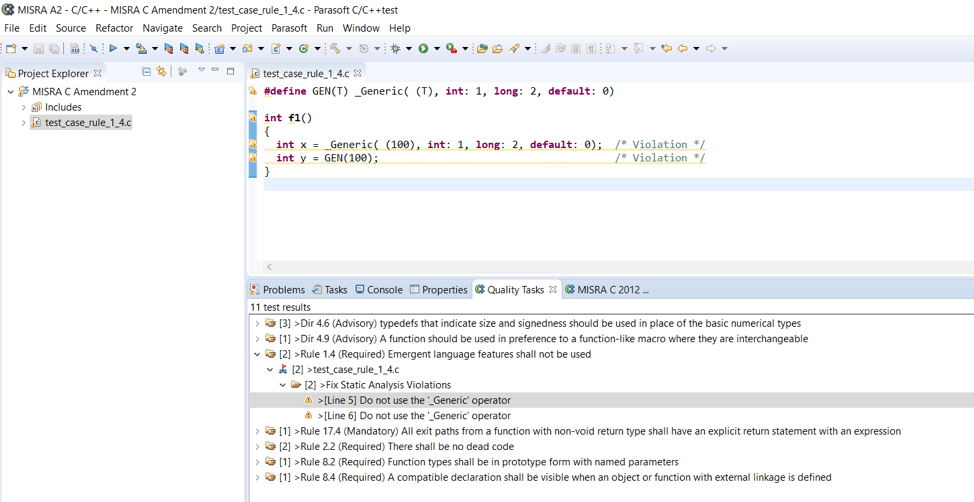
Figure 1: Parasoft C/C++test Identifies all MISRA Amendment 2 Rule violations
"MISRA", "MISRA C" and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.