Take a faster, smarter path to AI-driven C/C++ test automation. Discover how >>

Innovative static code analysis tools drive continuous quality for software development. Compliance automation with a range of coding standards delivers high-quality, safe, and secure coding for enterprise and embedded software development.
Static analysis is the process of analyzing source code for the purpose of finding bugs and evaluating code quality without the need to execute it. Developers and testers run static analysis on partially complete code, libraries, and third-party source code.
Static code analyzers use a compiler-like front-end to build a syntactic and semantic model of the software. The syntactic model is then analyzed against a set of rules or “checkers” to see if the code is in violation. These checkers use pattern-matching algorithms to detect errors including:
Static analysis is highly recommended or required by some companies building applications to safety standards like ISO 26262, DO-178C, IEC 62304, IEC 61508, and EN 50716. It helps organizations detect hard-to-find defects and improve software safety, security, and reliability by conforming to coding standards such as MISRA, AUTOSAR C++ 14, CERT, CWE, OWASP, and others.
“MISRA”, “MISRA C” and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.
Static code analyzers use a compiler-like front end to build a syntactic and semantic model of the software. The syntactic model is then analyzed against a set of rules or “checkers” to see if the code is in violation.
The checkers use pattern-matching algorithms to detect errors like poor use of language constructs, use of insecure functions, and violations of coding guidelines. The specific set of checkers used is configurable by the user. Some static analysis tools provide pre-set configurations for convenience, for instance, for coding standards such as MISRA C 2023.
More sophisticated checkers employ semantic analysis that uses data and control flow to detect complex bugs and security vulnerabilities. To do this, the static analyzer builds an execution model of the software, considers possible paths through the code, and evaluates use of data as it flows from source (like user input) to its destination (such as an API call or system call).
Analyzing every single possible condition and path would be too time consuming, so the analyzer uses heuristics to detect the most likely paths for evaluation. Types of errors detected by these checkers include null pointer deference, buffer overflows, and security vulnerabilities like command and SQL injections.
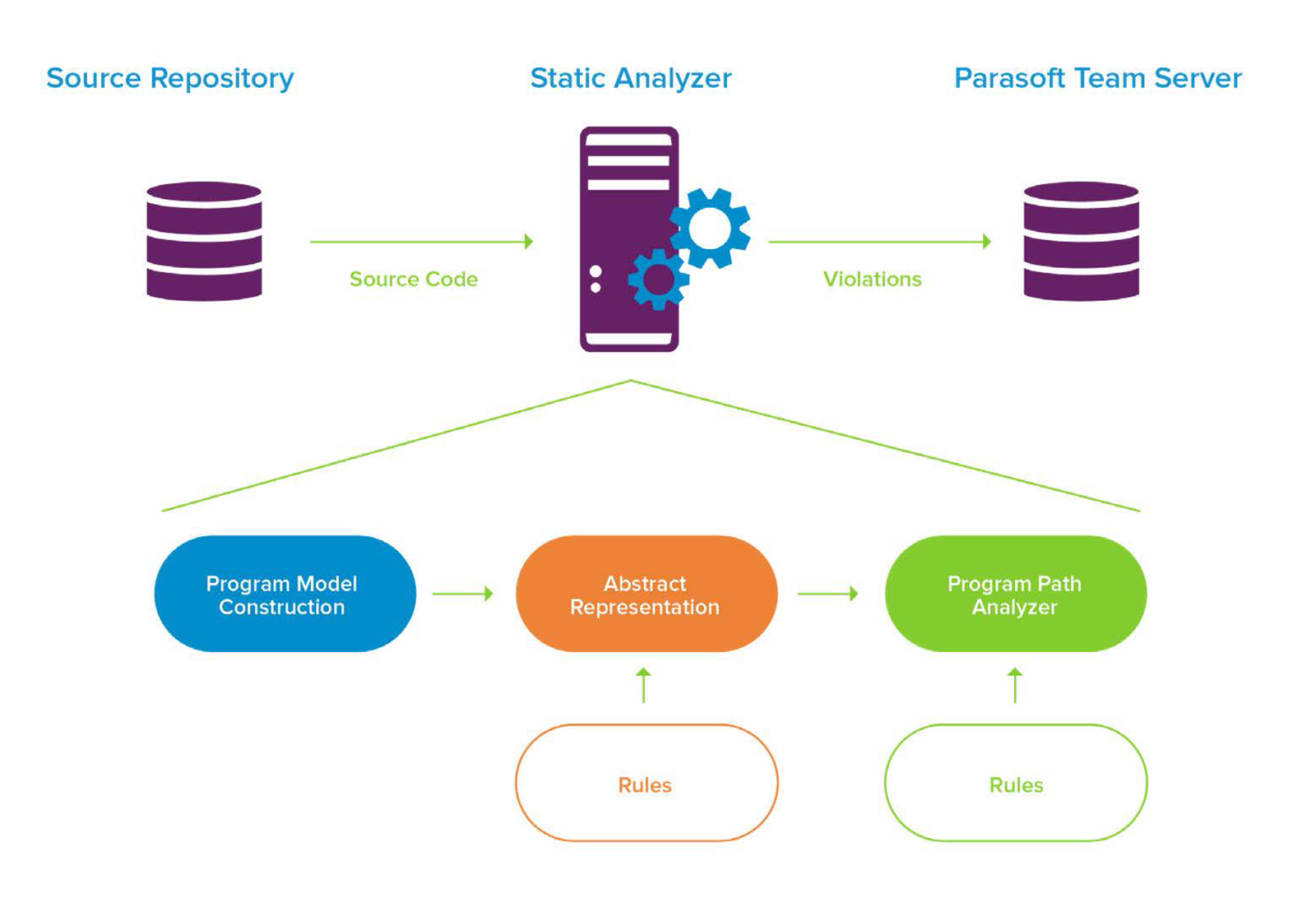
A high level view of the static analysis process
Teams most often use static analysis in two ways:
Some commercial tools integrate with leading IDEs and provide solutions for users to effectively manage analysis results. In fact, artificial intelligence and machine learning can also be applied in the prioritization and management of all identified violations to reduce effort and risk.
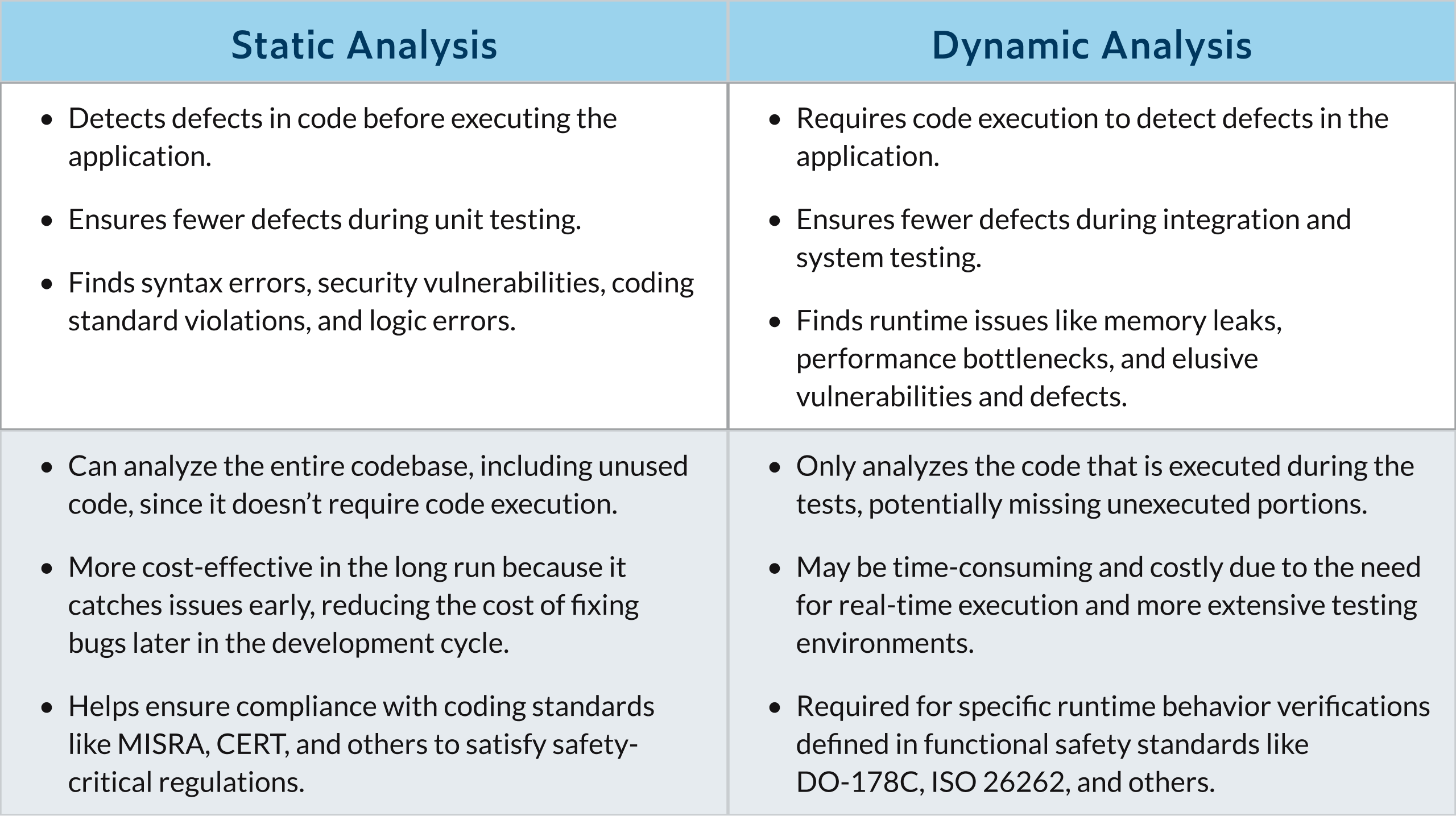
Combining static and dynamic analysis is the best option for getting actionable results, reducing bug occurrences, increasing bug detection, and creating more secure code overall. One is not better or worse than the other. They work in tandem like all the gears of a perfectly crafted Swiss watch.
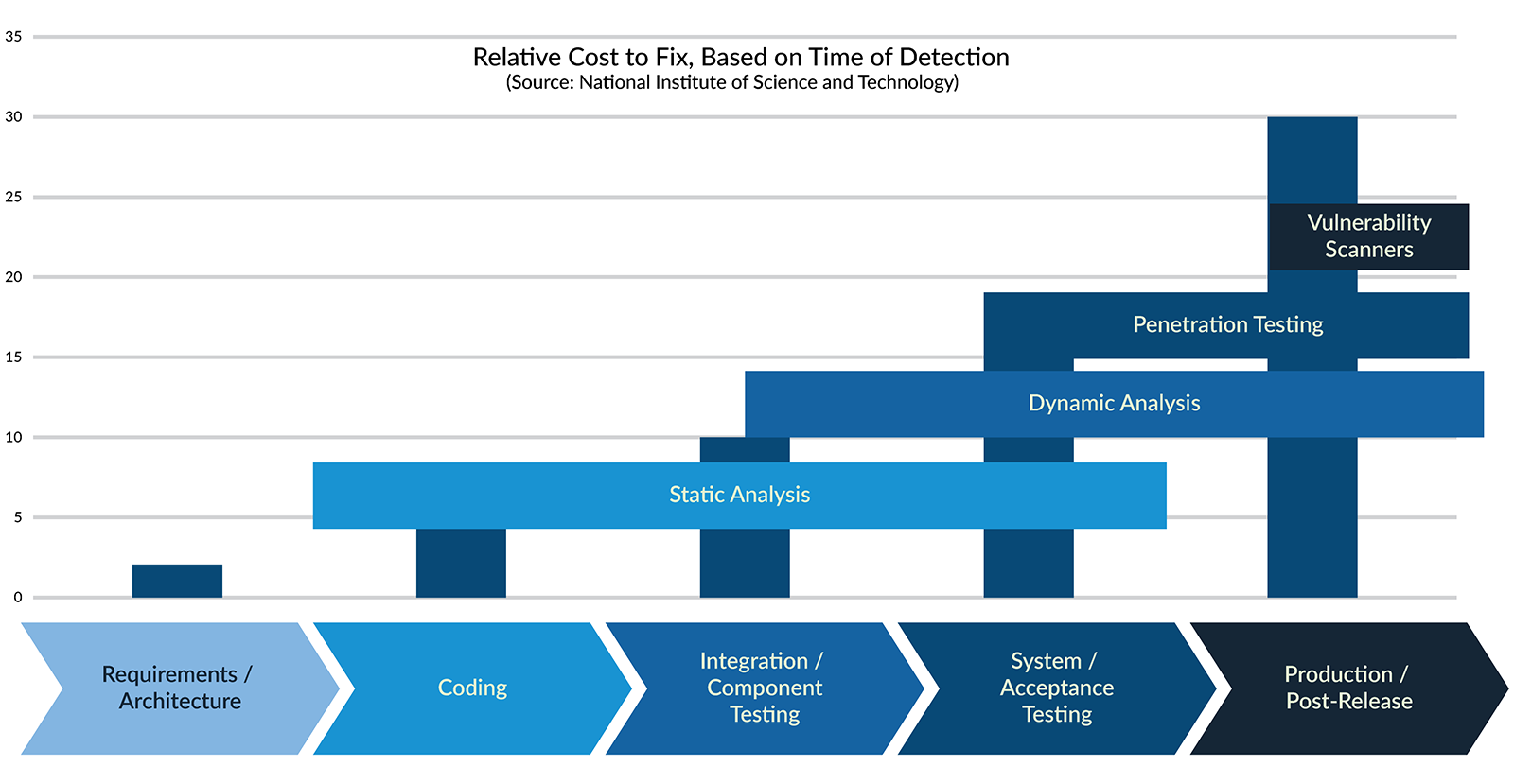
The SDLC pipeline and what stages static analysis and dynamic analysis find defects.
Static analysis is the process of examining source without the need for execution for the purposes of finding bugs or evaluating code quality. This means that teams can run static analysis on partially complete code, libraries, and third-party source code. In the application security domain, static analysis goes by the term static application security testing (SAST).
Looks for code patterns that violate defined coding rules. In addition to ensuring that code meets uniform expectations for regulatory compliance or internal initiatives, it also helps teams prevent defects like resource leaks, performance and security issues, logical errors, and API misuse.
Involves finding and analyzing the various paths that can be taken through the code both by control (the order in which lines can be executed) and by data (the sequences in which a variable or similar entity can be created, changed, used and destroyed). This can expose problems that lead to critical defects such as memory corruptions (buffer overwrites), memory access violations, null pointer dereferences, race conditions or deadlocks. It can also detect security issues by pointing out paths that bypass security-critical code, for example, code that performs authentication or encryption.
Involves measuring and visualizing various aspects of the code. It can help detect existing defects, but more often it warns of potential difficulty in preventing and detecting future defects when code is maintained. This is done by finding complexity and unwieldiness such as:
Checking for duplicate code helps organizations improve application design and decrease maintenance costs. During this type of analysis, code is parsed into smaller language elements (tokens). The tokens are analyzed according to a set of rules that specify what should be considered duplicate code. There are two types of rules:
Prevent code defects early in any development process before they turn into more expensive challenges in the later stages of software testing.
Usher in static analysis solutions that are recommended by process standards such as ISO 26262, DO-178C, IEC 62304, IEC 61508, EN 50716 or EN 50128, and more.
Weave compliance with security coding standards like SEI CERT, CWE, OWASP, DISA-ASD-STIG, and UL 2900 into the SA testing processes and to be certain that your code meets stringent security standards.
Establish compliance with safety coding standards such as MISRA, AUTOSAR C++ 14, JSF, and more, or create your own custom coding standards configuration for your organization.
Easily integrate static analysis into your streamlined CI/CD pipeline with continuous testing that quickly delivers high-quality software.
Incorporate artificial intelligence and machine learning to improve productivity in your team’s static analysis workflow. The AI will flag and prioritize the most urgent violations that need to be fixed first.
One of the best things you can do to be successful is to understand the four main types of static code analysis and the errors these tests are designed to detect.
Performance tests identify errors that will address overall performance issues and help developers keep up with the latest best practices.
Security-related source code analysis finds security risks like weak cryptography, configuration problems, and framework-specific command injection errors.
Safety and reliability tests help prevent issues with functionality because no one wants off-hour emergency unresponsive service messages. This type of static code analysis is especially useful for finding memory leaks or threading problems.
Style tests encourage teams to adopt uniform coding styles for ease of use, understanding, and bug fixing. Developers don’t have to waste time identifying style violations. The tests find them, which saves time.
Maximize the effectiveness of static code analysis to improve code quality, reduce defects, and meet compliance requirements efficiently by following these best practices.
The key to successfully running static analysis is an easy-to-use, accessible tool that gives developers useful, actionable information upfront without overwhelming them.

WHITEPAPER

BLOG
3 min read

WEBINAR
35 min watch

BLOG
3 min read

WHITEPAPER

DEMO WITH Q&A
