See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>


See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>
The automotive industry continues to rapidly evolve and grow into technical areas where other industries have operated for many years. For example, NASA’s Jet Propulsion Laboratory releases code fixes and new functionality currently in development for a spacecraft millions of miles away, en route to its destination. Similarly, we find the automotive industry providing software updates on cars that have been sold and are being driven by their consumers all around the world.
The future of self-driving cars also looks promising, with potential for widespread adoption in the next few decades. Several companies, including Waymo, Tesla, Uber, and traditional car manufacturers like GM and Ford, are at the forefront of developing self-driving technology. Many are conducting extensive testing, and some have deployed pilot programs in select cities. As the technology matures, it is expected to revolutionize transportation, making it safer, more efficient, and accessible.
This type of evolution—particularly that of advanced driver-assistance systems (ADAS)—comes with a new set of challenges in safety and security. Standards like ISO 26262 address functional safety of the development of electric and electronic systems (E/E), which include propulsion, dynamic control systems, and driver assistance.
Additionally, platforms like AUTOSAR provide an open standardized software layer architecture that further improves safety. They include guidelines for the use of the C++14 language in development of critical and safety-related systems. However, manufacturers have realized that due to the increased complexity and unknowns of modern technologies working together, along with changes in the internal and external environment, safety and security concerns have arisen that these standards don’t address.
When addressing ISO 21343, it’s important to understand that the recommended security consideration for cybersecurity should be integrated into your existing development processes. ISO 21434 references ISO 26262 in consideration of having these two disciplines take an interdisciplinary exchange of strategies, coordination and even tools used. This means that your organization should have your system engineers work with your security engineers through the requirements analysis phase for safety and security.
In parallel, perform hazard analysis and risk assessment (HARA) for safety, and threat analysis and risk assessment (TARA) for security. Nonetheless, a strong collaborative environment is needed to ensure a safe and secure result.
Ensuring security at the software implementation phase starts by applying static code analysis. The MISRA coding standard incorporates security guidelines, but you can also augment and strengthen code security by adopting CERT.
Continuing up the right side of the V, perform unit testing of all your low-level security requirements. In the next phase, create test cases that incorporate additional functionality. These test cases ensure that your high-level requirements are satisfied.
Moving to system testing, create system tests to ensure that the system requirements are verified. Confirm that all the test cases trace back to your requirements. This guarantees that no requirement goes untested. However, to safeguard that each requirement is fully tested, incorporate structural code coverage as recommended by ISO 21434 and ISO 26262. Code coverage not only ensures that every line of code has been tested, but it also ensures that your security test cases fully cover every possible path of execution through its security functionality remediation measures.
To overcome safety and security challenges, teams can turn to solutions like Parasoft C/C++test, which has been certified by TÜV SÜD for use in safety-critical applications per ISO 26262 and for ISO 21434 through association. Both of these standards recommend performing static analysis, dynamic analysis—which includes unit, integration, and system testing—code coverage, and requirements traceability. Offering exactly what ISO 26262 and ISO 21434 recommend for software verification in safety and security, Parasoft also provides the documentation required to prove compliance with both standards.
The United Nations Economic Commission for Europe (UNECE) released regulatory requirements on June 23, 2020, where they outlined new processes and technologies that automotive manufacturers must incorporate into both their organization and vehicles. These regulations also apply to Tier 1 and Tier 2 suppliers of software and hardware components, including mobile services.
Vehicle manufacturers are required to put into the organizational structure a risk-based management framework for discovering, analyzing, and protecting against relevant threats, vulnerabilities, and cyberattacks.
The following categories require cybersecurity testing and passing inspections.
A passing grade on both organizational and vehicle WP.29 key requirements means that the manufacturer receives a certificate of compliance. New vehicles without this certificate cannot be sold in the EU after July 2024. Be aware that the United States does not participate or have its own similar regulations. However, the writing is on the wall.
Automotive Software Process Improvement and Capability Determination (ASPICE) provides a measurement framework for independent assessors to evaluate an organization’s capability for software development. Ensuring software safety and cybersecurity does not only lie within the technical engineering aspects of the development of the electronic system, but also requires the organization to incorporate processes and checks.
These processes and checks must include ways to track and monitor progress within all practices of the organization to ensure:
This is also one of the two key certification criteria for UNECE WP.29 on organizational cybersecurity capability.
It’s brought to fruition other outgrowths from ISO 26262, like ISO/PAS 21448 more commonly referred to as SOTIF (safety of the intended functionality). SOTIF helps you analyze and prevent the misuse of the intended functionality where it creates an unsafe scenario. For example, your vehicle inadvertently shuts down while you’re driving it, due to an initiated software update.
Security vulnerabilities also pose unsafe scenarios. An attacker could use the car’s Wi-Fi connection to remotely exploit an exposed port. They could somehow work their way from the advanced in-vehicle infotainment (IVI) into taking control of, or influencing, safety-critical components like braking or steering due to sharing the same communications infrastructure.
Standards like SAE J3061, superseded by ISO/SAE 21434, specify that an initial Threat Analysis and Risk Assessment (TARA) be completed to assess potential threats related to operation, privacy, and other factors where a road user/driver can be impacted. If the risk for any threat is sufficiently high, then a cybersecurity process is necessary. There are various approaches to flushing out security vulnerabilities and requirements that mitigate the risks. Learn more about TARA and why your development team needs TARA.
Standards like UL 4600 now exist specifically for fully autonomous vehicle operation. This means that there is no human supervision, and the autonomy assumes full responsibility. This standard focuses on building a safety case for the deployment of SAE Level 4/5 vehicles, not on how to test safety of autonomous vehicles on public roads. That would involve a different standard.
These standards and others play a crucial role in safety and security for the automotive industry. OEMs carry the liability costs for delivering unsafe and insecure vehicles to the masses. To mitigate these risks, OEMs need to adopt and adhere to these standards. However, OEMs should mandate the same quality and adherence by their suppliers. A weakness in one component can undermine the safety and security of the entire system.
Working with some of its automotive OEMs, Parasoft has built custom coding standards that incorporate MISRA, AUTOSAR C++14, CERT, CWE, and other custom rules to be used by their suppliers. This ensures that the same level of quality software exists across the entire supply chain.
Parasoft C/C++test is a unified testing solution that includes unit testing and structural code coverage as part of its functionality. This solution for C/C++ software development supports a comprehensive set of hardware targets and development ecosystems that suppliers and OEMs can use with varying development infrastructures. C/C++test has been certified by TÜV SÜD for use on safety and security-critical systems. For ADAS and secure connected cars, C/C++test’s seamless integrations with SOAtest and Virtualize combine API testing with runtime application coverage and simulated virtual test beds.
ISO 26262 is a functional safety standard that covers the entire automotive product development process. It includes activities such as requirements specification, design, implementation, integration, verification, validation, and configuration.
The standard provides guidance on automotive safety lifecycle activities by specifying the following requirements:
ISO 26262 is an adaptation of IEC 61508 for the automotive industry. IEC 61508 is a basic functional industrial safety standard for electrical, electronic, and programmable electronic devices, and applicable to all kinds of industries. Other sectors like Medical IEC 62304 and Railway EN 50128/EN 50716 have also been derived from IEC 61508.
Since ISO 26262 has been extracted and expanded from IEC 61508 for the automotive industry, by inheritance it is a functional safety standard that provides guidance for regulating the entire product lifecycle process, at the software and hardware level from conceptual development through to decommissioning. It covers electrical and electronic automotive systems and their development process, including requirements specification, design, implementation, integration, verification, validation, and configuration.
The latest release, ISO 26262:2018 is subdivided into 12 parts. The standard has been evolving since its first edition, released back in 2011.
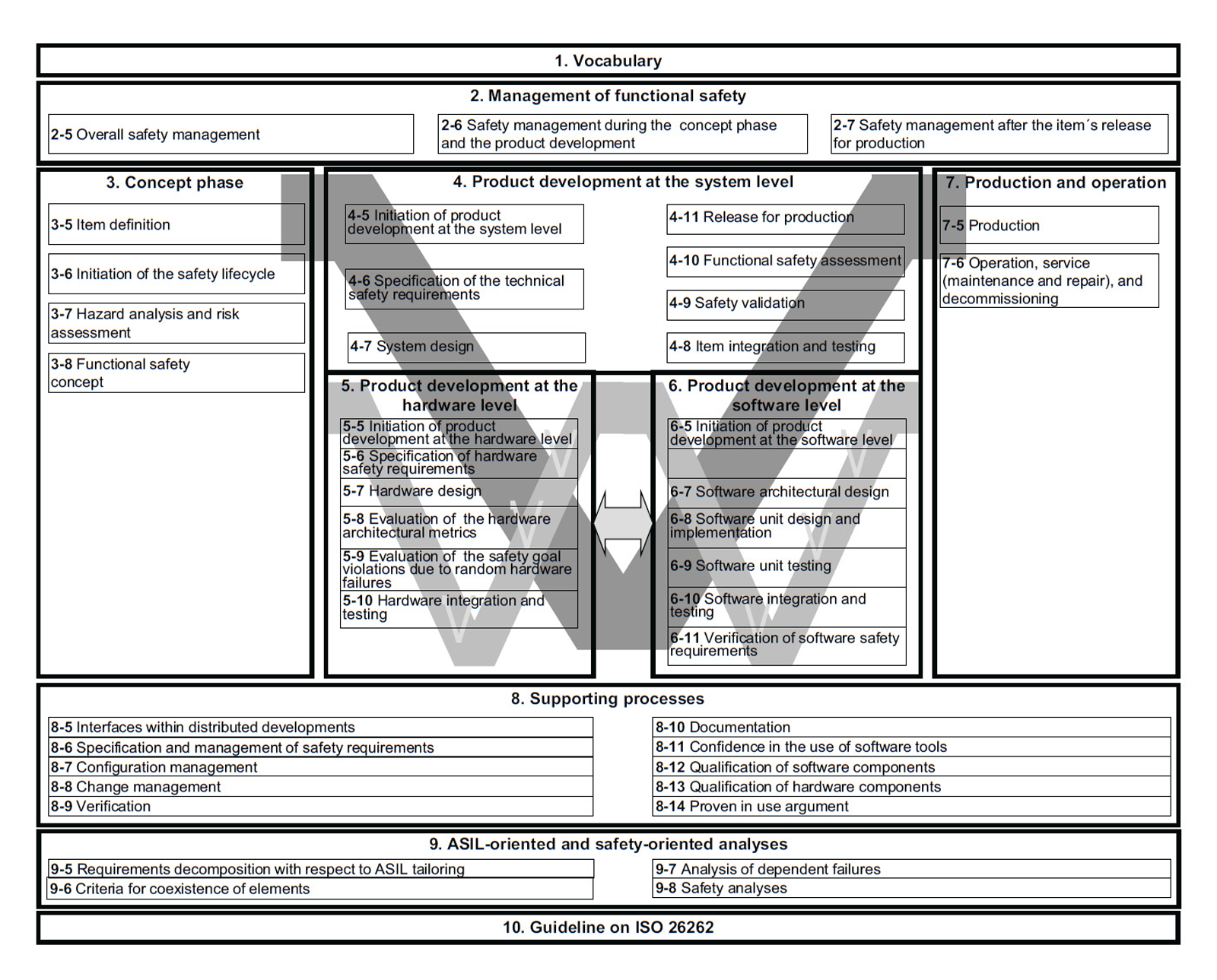
| Part 1 | Vocabulary section for the standard. Terms, definitions, and abbreviations are found here. |
| Part 2 | Management of functional safety, which defines an internal functional safety process for the team or company. This includes having a safety organization that oversees the planning, coordinating and documentation activities related to functional safety. |
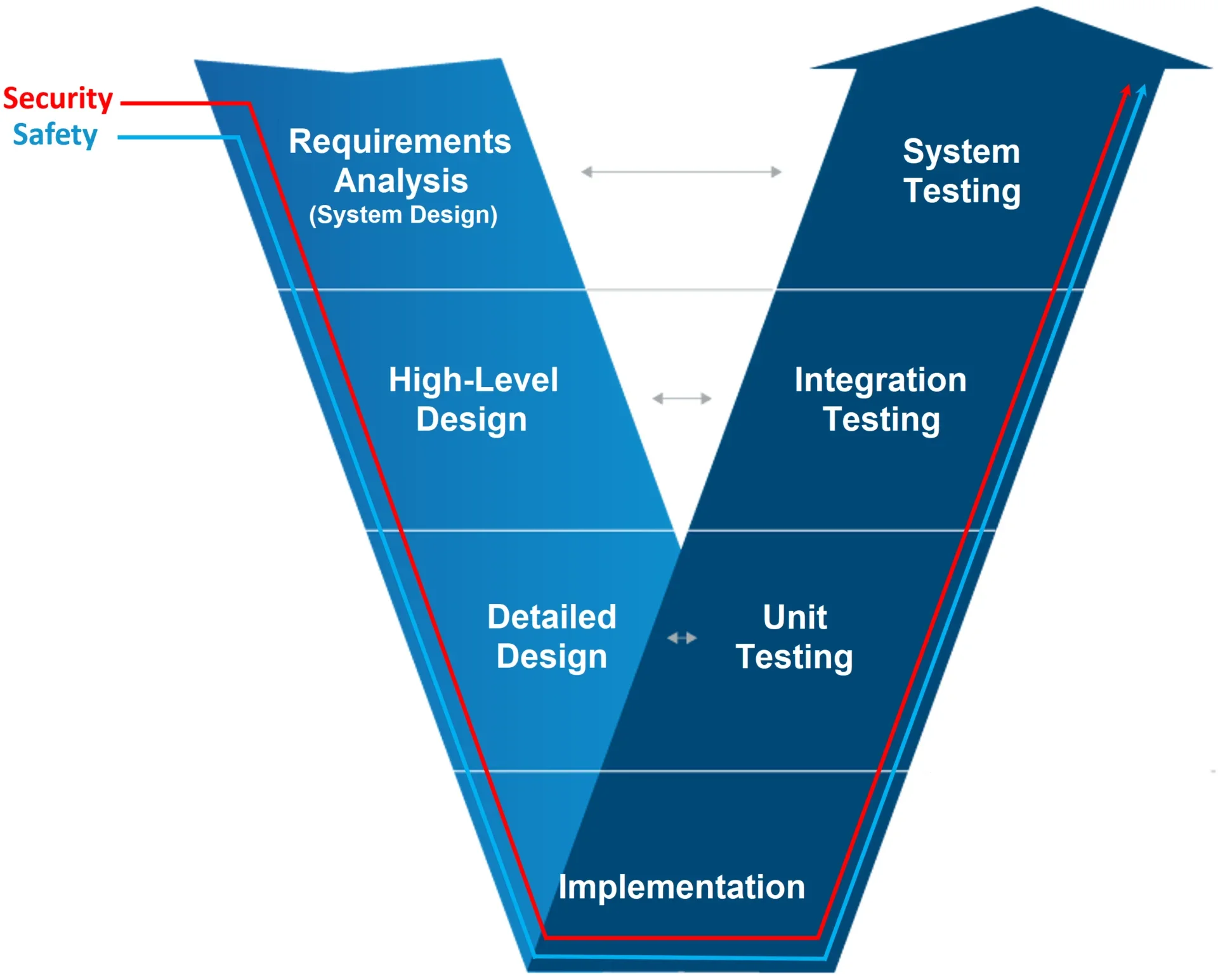
| Part 3 | The concept phase that takes in the stakeholder requirements and drives what you are going to build and ultimately deliver. In the Overview of ISO 26262 image, notice on the right side of the concept phase box the beginning of a gray-shaded V watermark. The shaded Vs represent the interconnection among parts 3, 4, 5, 6, and 7 of the standard. These part series are based upon the V-model software development lifecycle. You have the different phases of development represented on the left and the verification and validation or testing phases on the right. If you are a systems or software engineer in the embedded industry, the V-model is well known. |
| Part 4 | Beginning of product development at the system level, which includes parts 5 and 6 but looking at these from a high level of abstraction. The architecture is defined, including functional test cases that verify and validate the architecture. To dive in deeper into the detail design and implementation, part 5 and part 6 are defined. |
| Part 5 | Part 5 targets development of hardware, which is out of scope for this document. |
| Part 6 | Targets software development. You can see a smaller lighter gray V watermark for software development and again the left-hand side of the V encapsulates the requirements decomposition, design, and implementation phases but now a much lower level of granularity. On the right-hand side of the V, sections 6.9, 6.10, and 6.11 represent the testing or verification and validation of the software. This includes unit testing, static analysis, structural code coverage, requirements traceability and more. It also includes requirements for the software development of automotive applications. This includes obligations for initiation of product development, specification of software safety requirements, software architectural design, software unit design and implementation. On the verification and validation of the software component, you have multiple methods recommended or mandated based on the assigned safety integrity level (ASIL). |
| Part 7 | Addresses the production and operation of the product, once it’s out in the field. This means you must consider things like maintenance and decommissioning or sunsetting of your product. |
| Part 8 | Specifies the various supporting processes and solutions needed in the development of the system that help ensure functional safety. This includes having a configuration management solution, a change management, a documentation management, and other solutions in place. Another important aspect of Part 8 is the qualification of the software tools being used. You don’t want to use an open source tool or an uncertified tool from a vendor that undermines the safety or security of your product by introducing issues. Use a tool that has been certified by the Technical Inspection Association (TUV) and has a proven in-use history or argument. |
| Part 9 | A critical section to understand because it pertains to assigning a risk classification on the system under development. This means that you have to take into consideration the risk to the passengers or pedestrians if the electrical or electronic system in development were to malfunction or fail. |
| Part 10 | An overview of the ISO 26262 standard with additional explanations that enhance the understanding and concepts of the other parts in the standard, so it's informative. |
| Part 11 | Adaptation of functional safety guidelines to semiconductors for automotive. It offers guidance and information to semiconductor manufacturers on how to develop ISO 26262 compliant IP. It helps incorporate functional safety because users of semiconductors may not know how to use the semiconductor safely. This came about because automotive systems have become very complex and semiconductors have enabled most of the recent innovations. That includes vision-based technology, enhanced graphics processing units (GPUs), application processors, sensors, DRAM, and other components that empower advanced driver-assistance systems or ADAS. |
| Part 12 | Adaptation of the standard for motorcycles, which has been intentionally left out of Figure 2-1 and this ebook. |
In ISO 26262, a hazard analysis and risk assessment (HARA) needs to be performed on the system under development. Upon completion of the HARA an ASIL is assigned to the software component and there are levels A through D. Level A represents the lowest hazard assignment and Level D represents the highest hazard assignment. Meaning that the failure of a system with ASIL D assignment could be catastrophic.
There is also a quality management (QM) level assignment, which means that there is no safety requirement. ASIL is assigned by taking the severity of the injury times the probability of the failure times the controllability. The following table spells out each level for severity, exposure, and controllability.
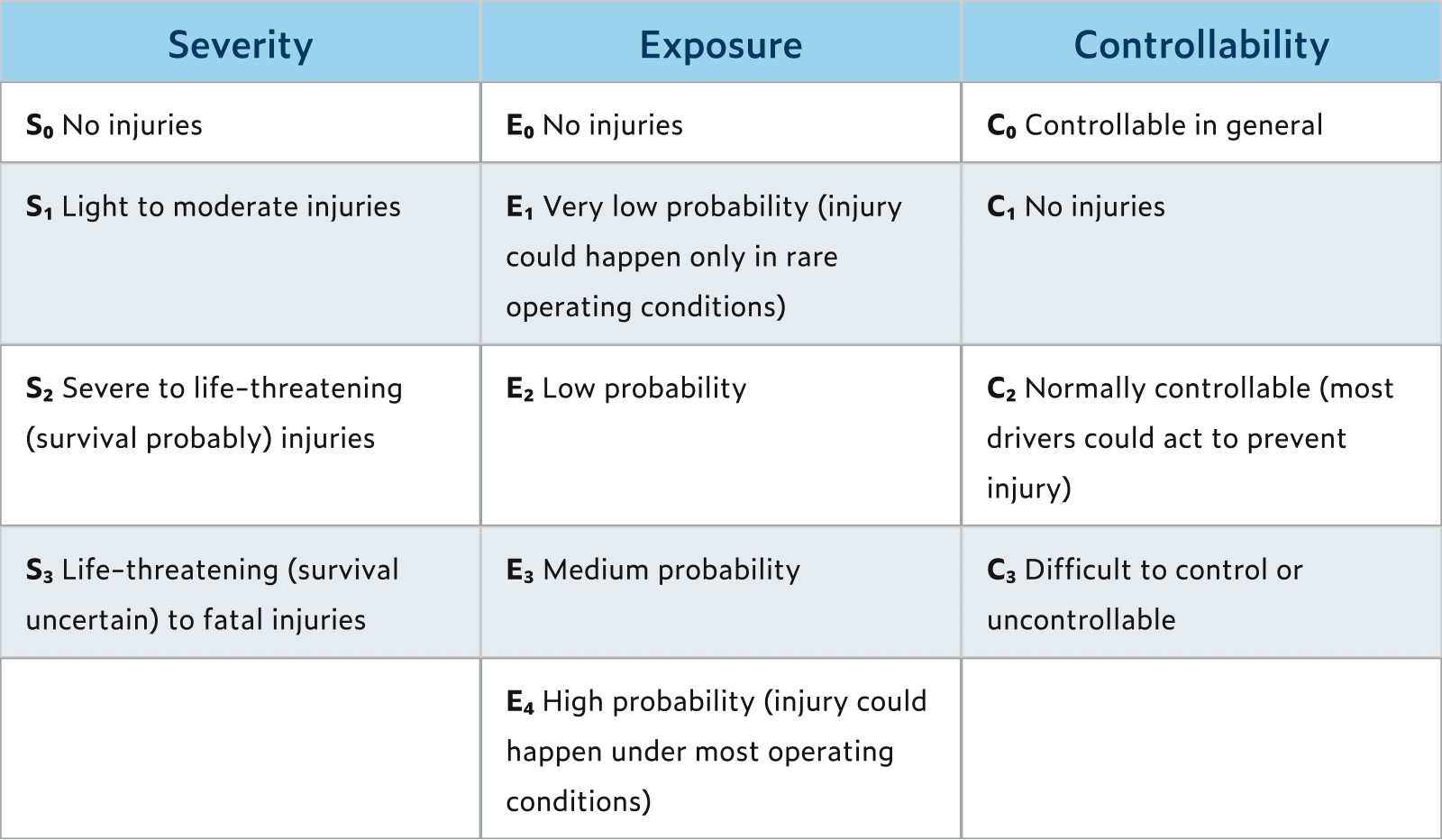
Exposure = The frequency or probability that the failure would occur.
Controllability – The extent to which we can ensure that the event doesn’t happen.
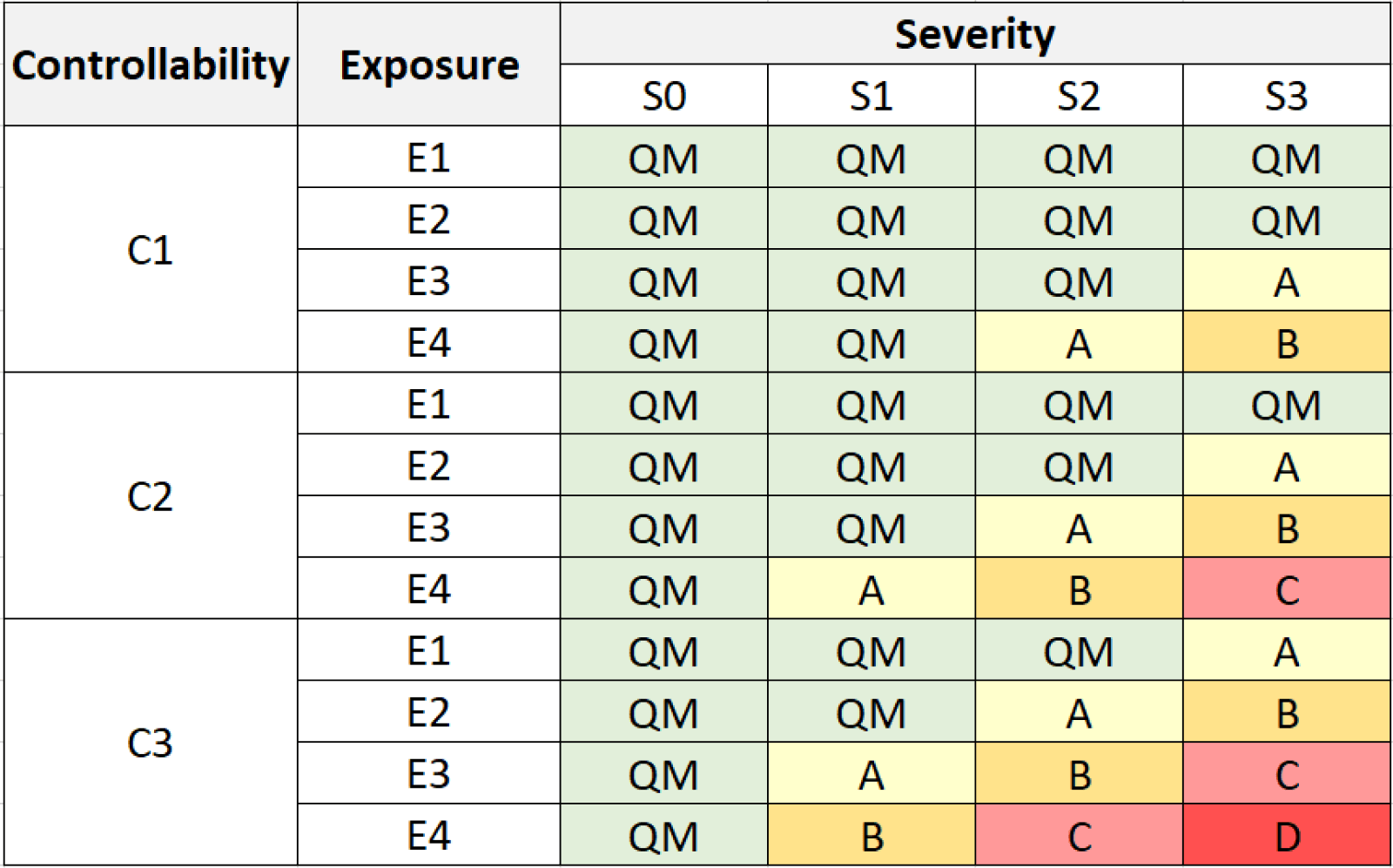
There are several tables freely made available that provide help in determining the ASIL value. The table below is an example of one that’s much easier to read and shows the ASIL levels in colors based on severity, exposure, and controllability.
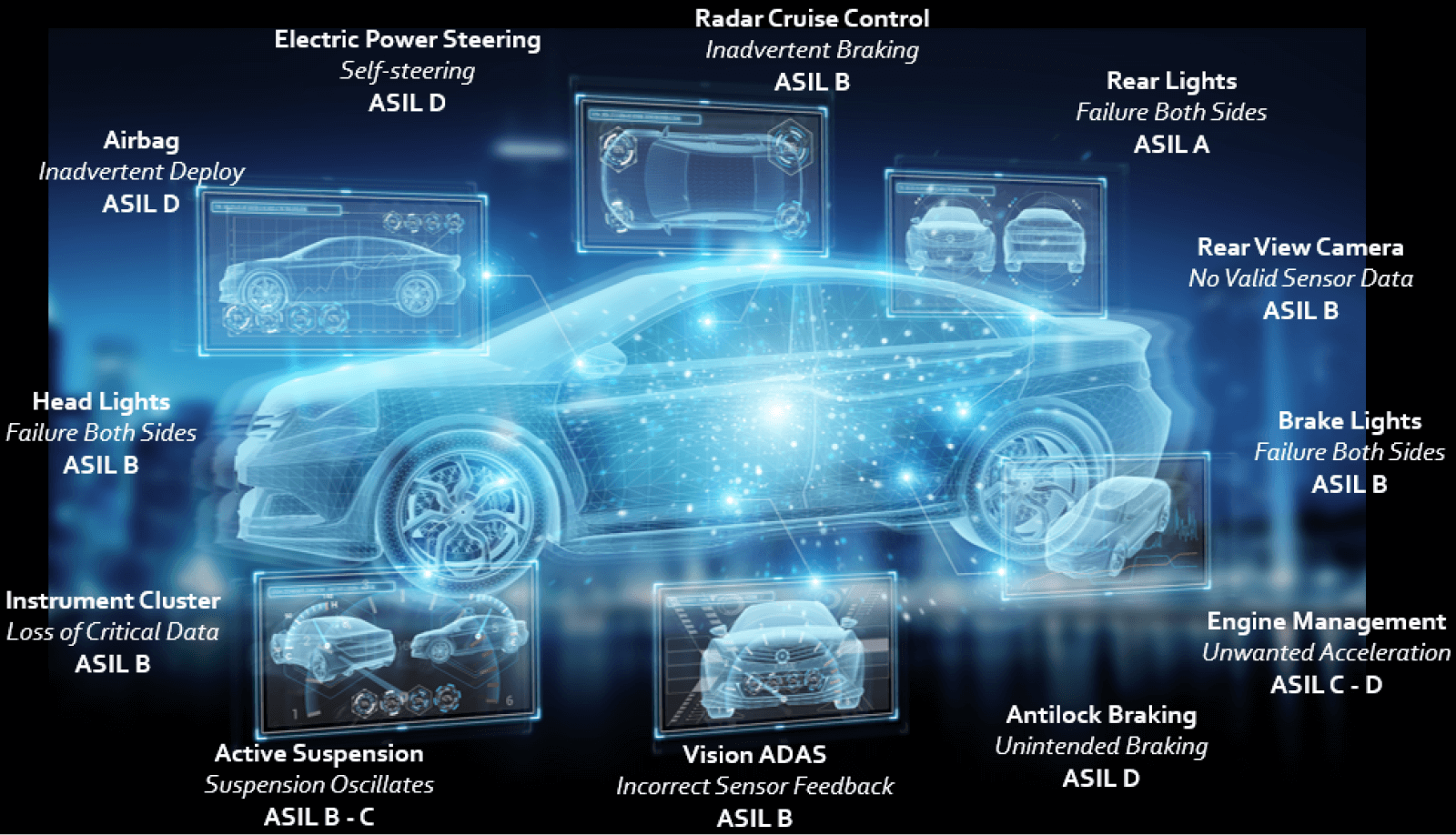
Roadside vehicles come with lots of safety systems, and some are considered active safety and others passive safety.
Active safety is used to refer to technology assisting in the prevention of a crash or accident. You have your traction control, anti-lock braking system, vision ADAS, and others.
Passive safety systems are to keep the passengers safe. For example, in case of a crash, you have airbags, and seatbelts. The electronic windshield wiper and instrument cluster are also passive safety systems.
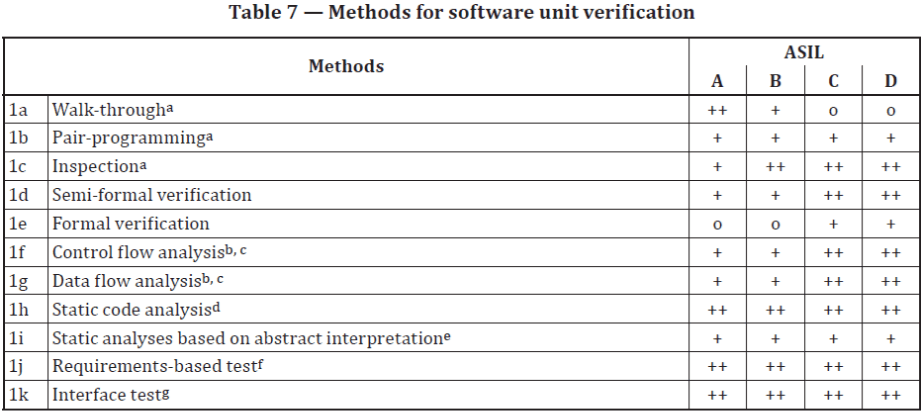
Since the focus of this guide is software, it’s important to cover the test verification and validation methods recommended by the standard. For example, Table 7 captures verification methods 1a through 1k to be applied during unit design and implementation. Method 1h, “Static code analysis” is highly recommended for ASIL levels A through D.
The columns in Table 7 on the right show A to D ASIL levels. A single “+” symbol indicates recommended by the standard, a double “++” indicates highly recommended, and an “o” indicates no recommendation.
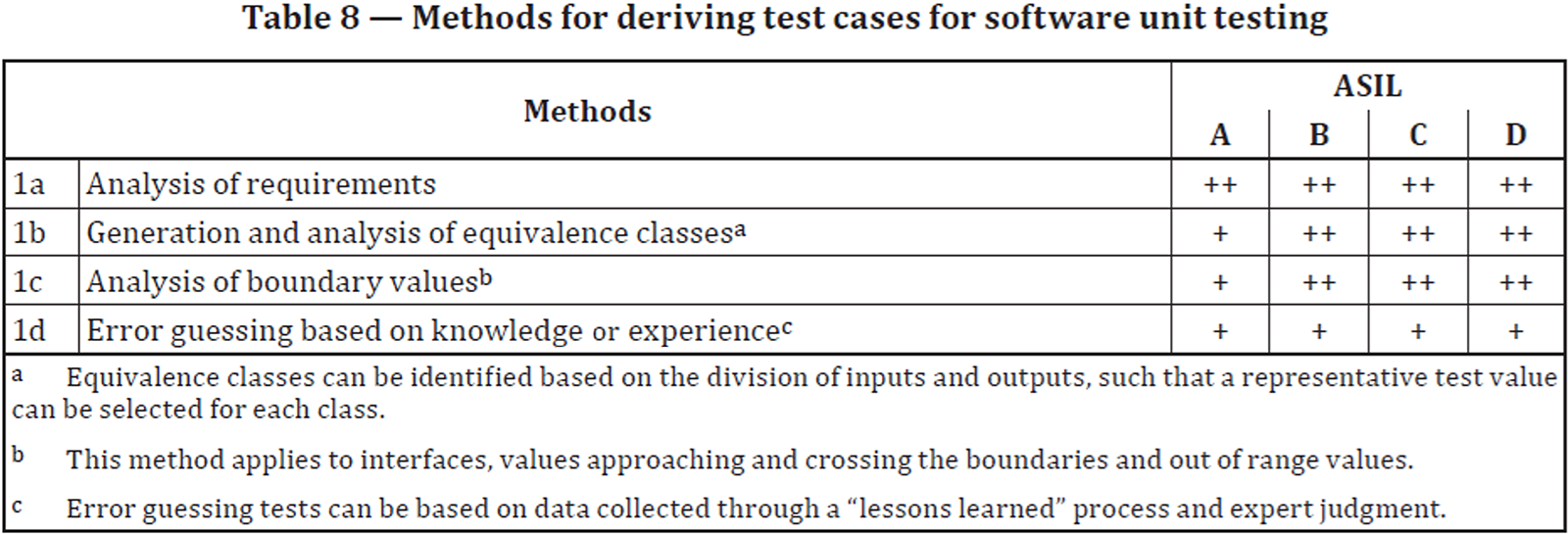
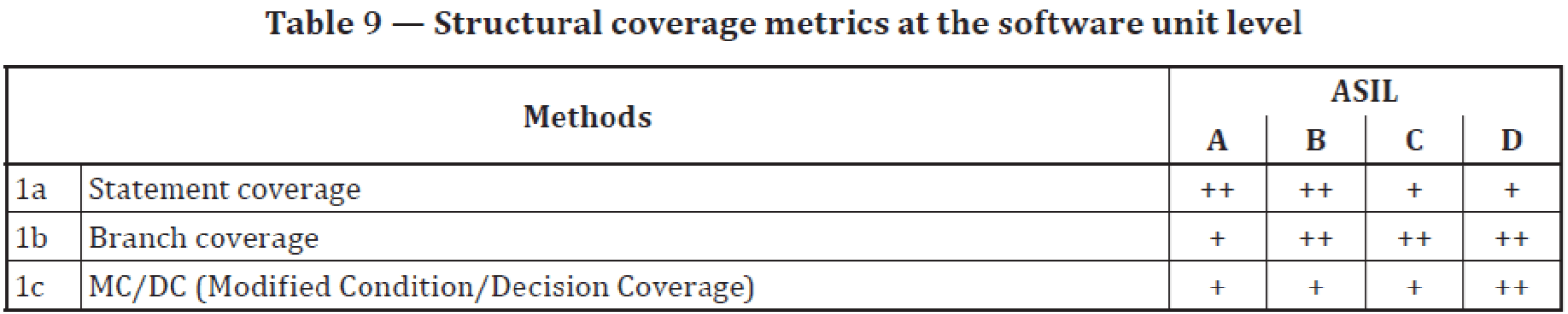


Explore the Chapters