Take a faster, smarter path to AI-driven C/C++ test automation. Discover how >>

Explore the Chapters
CWE is a list of discovered software weaknesses based on the analysis of reported vulnerabilities (CVEs). The collection of CVEs and CWEs is a U.S. government-funded initiative developed by the software community and managed by the MITRE organization. In its entirety, the CWE list contains over 800 items.
These 800+ items are organized into more usable lists such as the well-known CWE Top 25. The Top 25 lists the most common and dangerous security weaknesses, which are all exploits that have a high chance of occurring and the impact of exploiting the weakness is large. The software weaknesses documented by a CWE is the software implicated in a set of discovered vulnerabilities (documented as CVEs) when analysis was performed to discover the root cause. CVEs are specific observed vulnerabilities in software products that have an exact definition of how to exploit them.
The current version of CWE Top 25 is from 2024. An updated Top 25 is currently in process with improved linking to CVEs and the NVD. Ranking considers real world information so that it truly represents the Top 25 application security issues today.
The current CWE Top 25 is listed below.
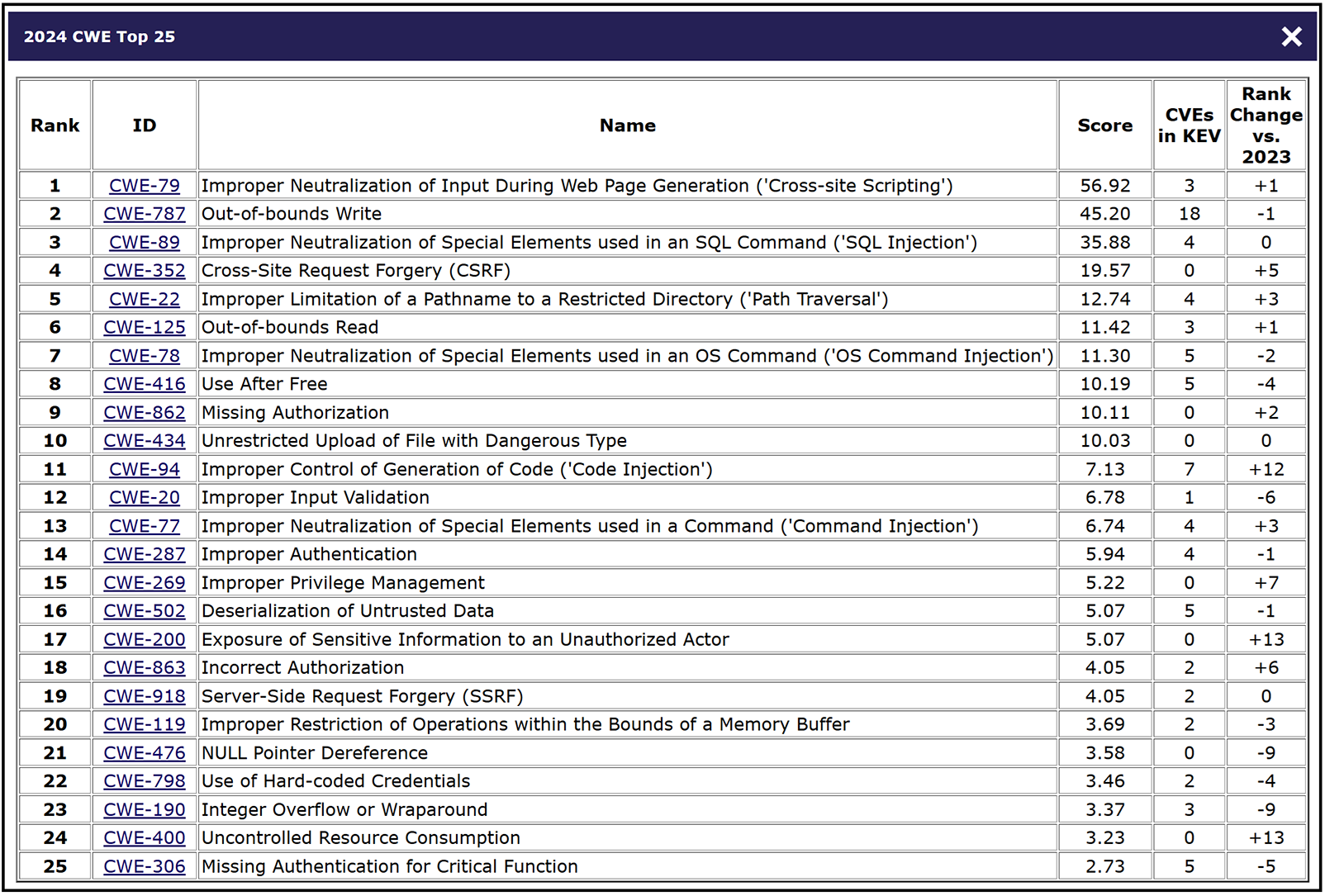
CWE Top 25 Most Dangerous Software Weaknesses
The CWE uses a risk scoring method to rank the Top 25 (and on the CUSP). This score takes into consideration the technical impact of a software weakness (how dangerous an exploit of the weakness is in the real world) as measured by the CWSS (common weakness scoring system). Examples of technical impacts from vulnerabilities may include denial of service (DoS), distributed denial of service (DDoS), read or write access to protected information, unauthorized access, and so on.
The details of these methods aren’t too important, but the sorted list is useful in understanding which vulnerabilities to be concerned about the most. As an example, it’s possible that your application is purely internal and DoS issues aren’t critical for you. Being able to prioritize the most important weaknesses of your application can help overcome overwhelm with static analysis violations.
Introducing the coding standard compliance process into the team development workflow is not an easy task. As such, it’s important to select a tool that will help in achieving compliance without imposing too much overhead and without the requirement for additional manual procedures. The following points are important decision-making factors when selecting the solution for static analysis.
The CWE Top 25 and its lesser-known sibling, On the Cusp, are not coding standards per se, but a list of weaknesses to avoid, improving security. To be CWE compliant, a project should be able to prove that it has made reasonable efforts to detect and avoid these common weaknesses.
Parasoft’s advanced static analysis tools for C, C++, Java, and .NET are officially compatible with CWE, providing automated detection of both Top 25 and On the Cusp weaknesses (and many more). CWE-centric dashboards give users quick access to standards violations and current project status. A built-in CWE Top 25 configuration is available for C, C++, .NET, and Java and has full coverage of all of the 25 common weaknesses.

CWE 4.4 – .NET compliance dashboard
The Parasoft tools include information from the CWRAF risk analysis framework, such as technical impact, so you can benefit from the same type of prioritization based on risk and technical impact and weaknesses found in your code.
The On the Cusp guidelines are also available. When enabled, they’re treated the same way as the Top 25 and reports provide the same level of detail. This is useful since the UL 2900 (formerly Underwriters Laboratory) and FDA recommends the full list of guidelines (Top 25 + On the Cusp + OWASP Top 10). It’s possible to integrate other guidelines from CWE lists or other standards and guidelines using Parasoft’s custom checker configurations as needed.
Parasoft also supports detailed compliance reporting to streamline audit processes. The web dashboards provide the link to compliance reports that provide a complete picture of where a project stands. In addition, the CWE Weakness Detection Plan maps the CWE entry against the checkers that are used to detect the weakness. This helps illustrate how compliance was achieved by an auditor, and the audit reports are available to download as PDFs for easy reporting.
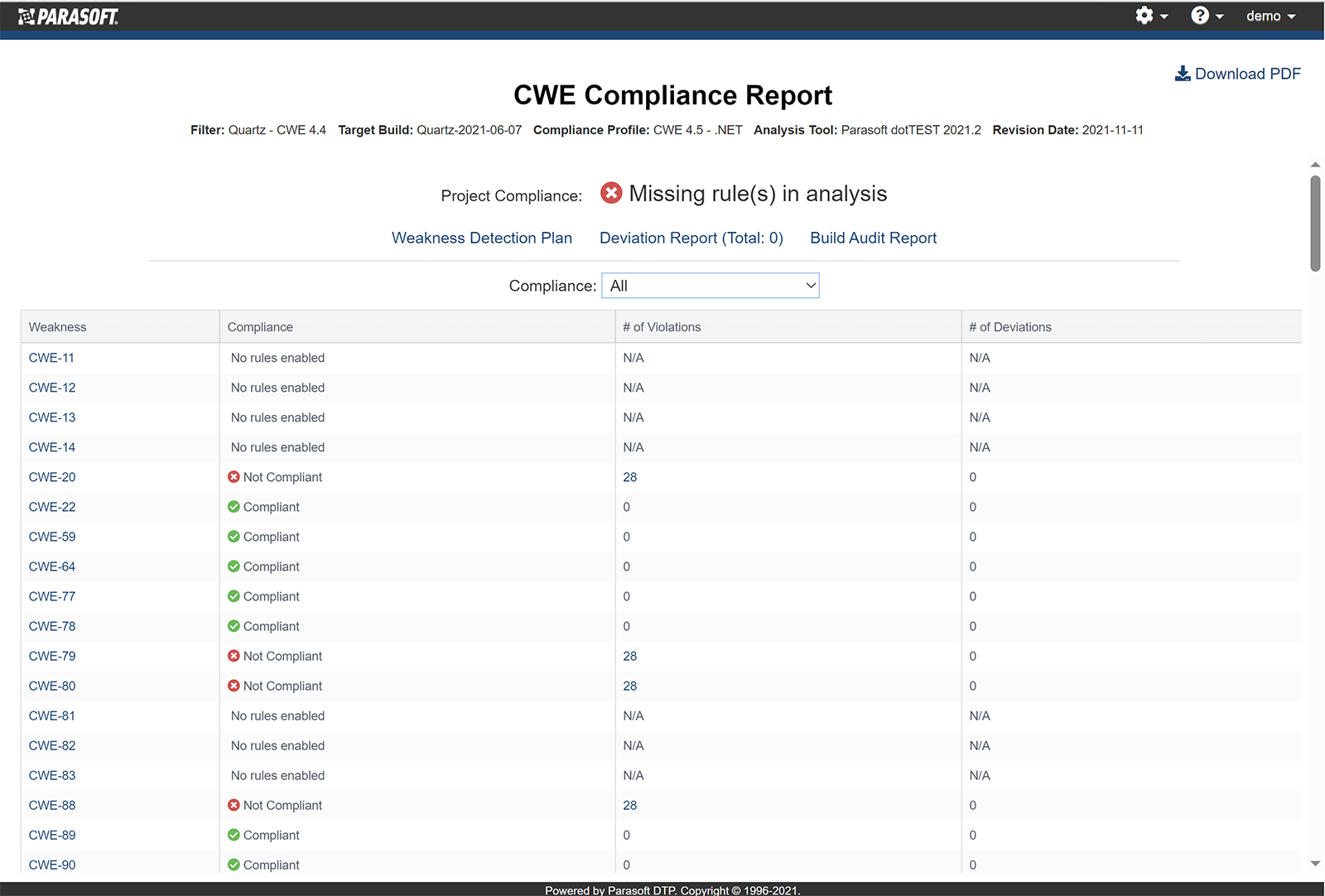
Auto-generated CWE compliance report

Explore the Chapters