Featured Webinar: Simplify Compliance Workflows With New C/C++test 2024.2 & AI-Driven Automation Watch Now
Jump to Section
SAST Tools: How to Choose the Right Solution
Making the right choice when it comes to choosing a static application security testing (SAST) solution can be a daunting task for IT professionals. In this post, we uncover all that you need to consider before making a choice.
Jump to Section
Jump to Section
Choosing the right static application security testing (SAST) solution is a critical decision in today’s ever-evolving landscape of software development and cybersecurity. As organizations increasingly rely on software applications to drive their operations, the need for robust security measures to protect sensitive data and mitigate potential vulnerabilities has never been more pressing.
With a plethora of SAST tools available in the market, the first challenge lies in identifying the solution that aligns with your specific needs, development workflows, and security requirements. Furthermore, as software development methodologies evolve, embracing Agile and DevOps practices, SAST solutions must also adapt to integrate seamlessly within these fast-paced development life cycles.
In this article, we’ll explore what SAST tools are, the key features, pros and cons, and best practices for integrating SAST tools into your software testing toolset.
What Are SAST Tools?
Static application security testing (SAST) tools are software testing tools used in the field of application security to identify and analyze security vulnerabilities in the source code or binary code of an application during implementation and before it is executed. SAST tools are usually employed early in the software development life cycle and help developers and security teams find and remediate security issues at the code level.
With SAST tools, developers can easily scan their source code or compiled codebase to identify potential security flaws, such as code vulnerabilities, insecure coding practices, and known security vulnerabilities. SAST tools use various analysis techniques, including data flow analysis, control flow analysis, and pattern matching, to detect issues like SQL injection, cross-site scripting (XSS), buffer overflows, and more.
It’s important to mention that the usefulness of SAST tools extends beyond mere detection; they also offer developers and security teams the advantage of early intervention. This is because when issues are detected when the code is being written or reviewed, it allows for quicker and more cost-effective remediation.
A SAST Solution With AI & ML
Parasoft brings in risk model data from standards such as OWASP, CWE, and CERT that are based on the likelihood of exploitation, impact to business, and so on to prioritize fixes even further. In addition, the Parasoft SAST solution’s embedded artificial intelligence (AI) identifies hotspots within the code base and machine learning (ML) easily predicts and prioritizes findings to help you focus on the right task.
Understanding SAST Tools and Their Importance
SAST tools are a vital part of a comprehensive approach to software security. These tools are designed to analyze the source code of software applications to identify potential security vulnerabilities and weaknesses. SAST operates without executing the application, allowing it to scrutinize the codebase and uncover issues during the early stages of the development process.
It scans for a wide array of security flaws, including code injection, data leakage, authentication vulnerabilities, and bad coding practices. The importance of SAST tools lies in their ability to prevent these vulnerabilities from making their way into the production environment.
Below are some of the key advantages of using SAST tools in software development.
Early detection of security vulnerabilities. SAST tools allow for the early identification of security vulnerabilities in the source code of an application. This proactive approach enables developers to address security issues during the development phase, reducing the cost and effort required to fix them in production. Early detection also helps prevent security vulnerabilities and data leaks from ending up in the product.
Integration into software development life cycle. SAST tools can be integrated into the software development process and incorporated into continuous integration/continuous deployment (CI/CD) pipelines. This means that security is not treated as a separate, standalone process but is instead woven into the fabric of the software development life cycle, making it more efficient, sustainable, and applicable to changes in security requirements.
Compliance and regulatory requirements. Many industries and applications are subject to regulatory requirements related to data security and privacy. SAST tools help organizations meet these compliance obligations by identifying and addressing security vulnerabilities, ultimately reducing legal and financial risks associated with noncompliance. In addition, SAST tools autogenerate the proof or documentation needed to demonstrate compliance and for any audit purposes.
Cost-effective security. SAST tools are a cost-effective way to enhance application security. It should be the first line of defense in detecting security vulnerabilities, because it’s automated and, in my experience, usually finds 60 – 80% of the same vulnerabilities as when performing other dynamic analysis security testing methods. Investing in SAST tools and practices early in the development process also prevents the need for expensive security patches and incident response efforts after a security breach has occurred.
Key Features of SAST Tools
Highlighted below are some of the features commonly found in SAST tools.
- Code analysis. SAST tools perform a comprehensive and in-depth analysis of the source code or binary code of an application. This analysis includes examining the code structure, control flow, and data flow to identify potential security vulnerabilities. The tools not only look for well-known vulnerabilities but also analyze the code for coding practices and patterns that might lead to security issues. This thorough code analysis helps uncover both common and hidden security flaws, enhancing the overall security posture of the application.
- Automated scanning. SAST tools are embedded with automation capabilities, making them suitable for scanning large and complex codebases. With automation at their core, SAST tools can systematically analyze source codes without human intervention when set to do so. Automation ensures that all parts of the code are examined, and it allows for frequent and regular security checks, contributing to a proactive security approach and reducing the chances of human error.
- Rule-based and pattern matching. SAST tools leverage predefined rules and pattern-matching techniques to detect vulnerabilities. These rules are based on security standards like OWASP, CWE, and CERT, coding best practices, and known attack patterns. Other popular coding standards like MISRA have also incorporated security as part of their guidelines. By applying these rules, SAST tools can flag code sections that exhibit behavior or structures known to be associated with security weaknesses. This approach streamlines the identification of issues and makes it easier for developers to understand and address them.
- Customizable rule sets. Many SAST tools provide organizations with the flexibility to customize, expand, or merge rule sets. This feature enables companies to tailor the tool to their specific coding standards, application requirements, and security policies. Customization is particularly valuable in situations where organizations have unique coding practices or security concerns that go beyond standard rules.
- Language support. SAST tools are versatile in terms of language support. They are designed to analyze code written in various programming languages, from commonly used languages like Java, C, C++, C#, VB.Net, and Python to less common or domain-specific languages. This broad language support ensures that SAST tools can be applied to a wide range of applications and development environments, making them a versatile choice for developers and security teams.
- Reporting and remediation guidance. SAST tools offer comprehensive compliance reporting capabilities that provide developers and security professionals with valuable insights. Reports not only highlight identified vulnerabilities but also include details such as the location of the vulnerability within the code, its severity, and potential impact.
Additionally, SAST tools often provide remediation guidance, suggesting specific code changes or best practices to mitigate the issue. This guidance empowers development teams to address security vulnerabilities efficiently and effectively, even if they are not security experts.
How SAST Tools Work
Understanding how SAST tools work helps you get a grasp of what to expect before incorporating SAST solutions into your stack. To make it easier, we have summarized the “how” in the steps below.
- Code scanning. SAST tools begin by scanning the entire codebase of an application. This can include the source code written in programming languages like Java, C, C++, C#, VB.NET, Python, and others. Some SAST tools can also analyze binary code and bytecode, making them versatile for a wide range of applications.
- Parsing and data flow analysis. After scanning the code, SAST tools use parsing techniques to break down the code into its constituent elements, such as functions, classes, and variables. They create an abstract syntax tree (AST) to understand the code’s structure. Then, perform data flow analysis to track the flow of data and variables through the code.
- Pattern matching. SAST tools use a database of known security vulnerabilities and coding patterns to compare the parsed code against these patterns and known vulnerabilities to identify instances where the code may be susceptible to common security issues.
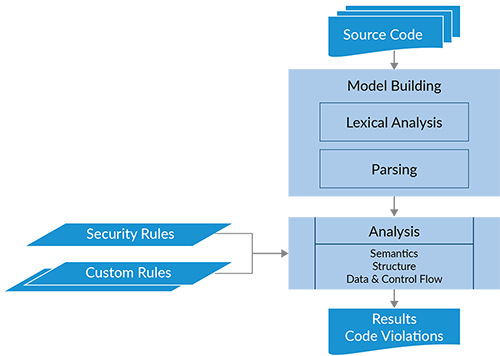
- Rule-based analysis. After the pattern matching, the tools apply a set of predefined rules and heuristics to the code to identify potential security flaws. These rules cover a wide range of issues, such as use of insecure libraries, SQL injection, cross-site scripting (XSS), and insecure authentication practices.
- Data and control flow analysis. At this phase, the tool analyzes how data is handled within the application and how control flows through the code. The analysis looks for instances where user inputs are not properly sanitized or validated, potentially leading to security vulnerabilities.
- Reporting and remediation. When vulnerabilities or potential issues are detected, SAST tools generate detailed reports, including the location in the code where the problem was found and a description of the issue including possible approaches to correcting the problem. Developers and security teams can use these reports to remediate the vulnerability and fix the code.
How Does SAST Fit Into Your Tool Chain?
SAST tools can be a great addition to your toolchain as they help to fortify the security of your software applications. To integrate SAST tools into your toolchain, it’s advisable to start by incorporating them within your CI/CD pipeline. This approach ensures that the tool automatically scans code as soon as changes are pushed to the repository, enabling real-time detection of security issues and preventing their propagation throughout the development life cycle.
Some SAST tools like Parasoft’s Jtest, C/C++test, and dotTEST can easily work with popular development technology stacks and also leverage AI and ML capabilities. The tools can streamline and automate security testing at an accelerated pace, making it possible for security teams and organizations to address the challenges of security and compliance validation more effectively. The developer-centric approach of Parasoft’s SAST tools enhances the developer experience by providing confidence in using SAST while coding and developing software, which in turn reduces security risks and long-term software maintenance costs.
Advantages of Using SAST Tools
SAST tools offer several advantages for the security of software applications. Some of its notable advantages include the following.
Improved Code Quality
One of the primary advantages of using SAST tools is the significant enhancement they bring to the overall code quality. SAST tools help identify coding best practices and facilitate adherence to coding standards. They pinpoint areas where code may be inefficient, difficult to maintain, or prone to errors, thus enabling developers to write cleaner, more maintainable code. This reduces the likelihood of introducing security vulnerabilities and results in more robust, efficient, safe, and sustainable software applications.
Early Identification of Vulnerabilities
SAST tools scrutinize the code during the development phase and identify security flaws before they have the chance to propagate further into the software development life cycle. This early intervention is crucial as it allows developers to rectify vulnerabilities at a stage when changes are more straightforward and less costly to implement. It also reduces the risk of vulnerabilities making their way into the production environment, thereby helping organizations safeguard their data and reputation.
Regulatory Compliance
For organizations operating in regulated industries, compliance with security standards and regulations is nonnegotiable. SAST tools aid in achieving and maintaining regulatory compliance by detecting security issues that may violate industry-specific requirements. They provide evidence of due diligence in code security, making it easier to satisfy auditors and regulatory authorities, thereby reducing legal and financial risks.
Easy to Scale
SAST tools are scalable and adaptable to the needs of diverse software projects and company sizes. Whether you are developing a small application or a large-scale enterprise system, these tools can be integrated into your development IDE (integrated development environment) or process seamlessly. Their capacity to analyze code in various programming languages and handle a range of project sizes makes them versatile and suitable for different development scenarios.
Highlights Code Problematics
SAST tools not only identify vulnerabilities but also pinpoint the exact location in the code where the issues exist. This level of precision is invaluable for developers, as it provides them with actionable insights that help them focus on specific areas that need attention, streamlining the remediation process.
Doesn’t Require Test Cases nor App Execution
Unlike some other security testing methods, SAST doesn’t necessitate test cases or the execution of the application. It operates solely by analyzing the codebase, making it well-suited for early-stage security assessments. This feature accelerates the identification and resolution of vulnerabilities, making it an efficient and cost-effective solution for secure software development.
Limitations and Challenges of SAST Tools
While SAST tools offer significant benefits, they come with limitations and challenges. We discuss some of them below.
False Positives and Negatives
One of the primary limitations of SAST tools is their propensity to generate both false positives and false negatives. False positives occur when the tool identifies a piece of code as a security issue when it is not. This can lead to wasted time and resources as developers investigate and address nonexistent problems. On the other hand, false negatives are equally problematic, as they represent genuine vulnerabilities that go undetected by the SAST tool. These missed issues can pose significant security risks if they are not identified and mitigated through other means. Striking the right balance in reducing false positives without increasing false negatives can be a challenging endeavor when using SAST tools.
Complexity of Static Analysis
The complexity of static code analysis can be a hurdle for SAST tools. Analyzing code without executing the application requires a deep understanding of the code’s structure, logic, and data flow. As software systems grow in complexity, SAST tools may struggle to keep up, potentially missing intricate security issues or generating false positives. Moreover, SAST tools may not be as effective at identifying vulnerabilities in certain types of code, such as complex data-driven web applications, where user inputs and interactions are dynamic and context-dependent.
Unsanitized Inputs
SAST tools heavily rely on code analysis, making them less effective at identifying vulnerabilities that arise from unsanitized inputs. If an application receives external input that is not properly validated and sanitized, SAST tools may not always detect this as a vulnerability during static analysis. Issues like SQL injection or cross-site scripting (XSS) that depend on user inputs may be challenging for SAST tools to pinpoint accurately.
Language Dependency
SAST tools are often language-dependent, meaning they may excel in analyzing code written in certain programming languages but may struggle with others. Some SAST tools are designed for specific languages, and their effectiveness can vary significantly across different language ecosystems. Organizations using a variety of programming languages in their projects may need to invest in multiple SAST tools or find a tool that supports their entire tech stack, which can be a logistical challenge.
How to Easily Adopt Security Testing
While some software engineers understand the importance of SAST tools in software security testing, the challenge has always been about how to make it work efficiently. For easy adoption of security testing with SAST, ensure the following:
Integrate SAST Tools Into the CI/CD Pipeline
Adopting security testing can be made easier when SAST tools are integrated into your CI/CD pipeline. This integration ensures that security checks are an integral part of your software development process rather than an isolated task.
When SAST is fused into the CI/CD pipeline, code is automatically scanned for security vulnerabilities with each code commit or build, providing near real-time feedback to developers. This not only accelerates vulnerability identification but also promotes a security-conscious culture within your development team. In addition, this integration also makes it easy to leverage the automation capabilities of CI/CD tools, which can trigger SAST scans at specific stages of your pipeline and make it a routine practice.
Regular Scan Schedules With SAST Tools
Establishing a regular and systematic scanning schedule with SAST tools is another key aspect of adopting security testing. Routine scans should be scheduled at predetermined intervals, such as daily or weekly, to ensure that all code changes are consistently checked for security vulnerabilities. Regularity is essential to catch any new issues introduced during development and to monitor the status of previously identified vulnerabilities.
Additionally, consider integrating scans into your code review process, making security checks an integral part of code reviews alongside functionality and design assessments. This reinforces the importance of security within your development team and provides an additional layer of scrutiny. When vulnerabilities are detected during scheduled scans, create a protocol for efficient remediation and tracking to ensure that identified issues are promptly addressed and resolved.
Keep SAST Tools and Its Vulnerability Database up to Date
Keeping the SAST tool and its vulnerability database up to date is essential for effective security testing as it enables the detection of the latest vulnerabilities and enhances accuracy in identifying real security issues while reducing false positives. As with every software tool, an updated version of SAST tools and vulnerability database ensures compliance with evolving coding standards and supports new technologies and changes in your codebase.
Build High-Quality Software by Detecting and Preventing Defects
As security is becoming a bigger issue, compliance is something you have to prove. Gone are the days when you can just say you ran a gaggle of tests and say your software’s clean. Now, you need to demonstrate that you took all the steps that the standard requires. And with Parasoft’s robust reporting, comprehensive testing, and advanced AI and ML capabilities, you can get all those capabilities right out of the box.
Incorporating Parasoft into your toolchain offers several key advantages, including rapid security and compliance validation, real-time awareness of software risks, immediate feedback and analytics for efficient remediation workflows, and the elimination of manual testing bottlenecks. Parasoft security testing solutions also provide deep insights and analytics to help you pinpoint the most critical security concerns and point you in the best direction toward proper remediation.




