See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>


See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>
Jump to Section
Don't let a hacker take advantage of an unchecked software vulnerability in your application. Leverage TARA to identify and mitigate cybersecurity risks and prevent costly breaches.
Jump to Section
Jump to Section
TARA, a.k.a. threat analysis and risk assessment, plays a critical role in software development and deployment. Whether you’re working under ISO 21434 for automotive components, IEC 62443 for working within medical devices, or even DO-326A in avionics, TARA methodologies should be effective and integratable into your SDLC and development ecosystem. A transformative evolution has been taking place in many industries. For example, Renovo had to address both safety and security challenges.
Choosing the right tools to supplement your TARA can mean the difference between enduring insecure products and services or delivering secure and safe software systems.
This blog answers the following questions:
Simply put, a threat analysis and risk assessment is a process to identify possible risk factors, vulnerabilities, and noncompliant elements of your software. It helps teams identify insecure spots or compliance issues with their software in a way that promotes mitigation and security implementation earlier into the SDLC.
Some may be familiar with CWE or common weakness enumeration which plays a role in approaching a TARA strategy. Software security depends on CWE as it makes vulnerability management more accessible and easier to digest. Though MITRE owns and maintains the CWE, it is a community-powered catalog of various risks across many industries including automotive.
One of the best examples of when a TARA is critical is with ISO 21434 compliance. As outlined in our blog about cybersecurity for the automotive industry, the TARA can identify weaknesses and guide teams on how to incorporate security measures in their development work. Ideally, a comprehensive and effective TARA will mitigate threats and make compliance more assured.
A well-executed TARA can save your team from avoidable vulnerability disasters or make the difference between meeting security requirements or not. In drastic cases, it can also be the difference in launching a product or service or having to backtrack, losing development time and money.
Think of it in the same way as getting your annual physical at the doctor every year. It’s a mild inconvenience that could help you spot an issue before it becomes a major problem, right? TARA empowers development teams to do exactly the same thing. The following image shows the process of the TARA method.
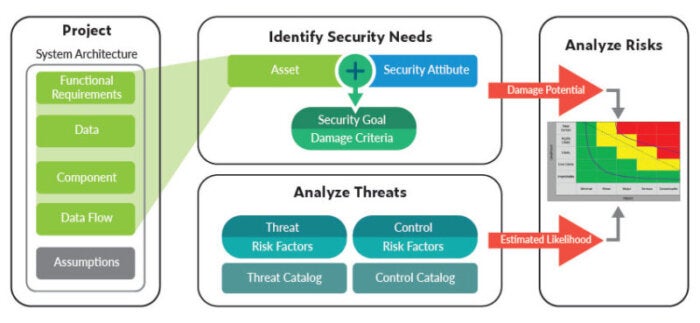
Step 1: Define the Project
Define what you’re building from its most basic function to its most complex feature. Be sure to catalog any assets involved such as network components, applications, and so on.
Step 2: Threat Identification & Risk Assessment
Trying to develop a strategy against risk without knowing the biggest threats is fruitless. Instead, first, identify the kinds of things that can go wrong with your project. Is your data protected? Are you vulnerable due to third-party libraries or APIs? Perhaps you must work with proprietary technology with very specific requirements.
No matter the situation, being aware of all the potential threat types and vectors is a crucial step in developing and incorporating a TARA strategy.
Step 3: Threat Mitigation
The next natural step is taking measures to mitigate any possible threats and risk vectors. This may entail incorporating SEI CERT, a security code analysis, into your CI/CD pipeline. Other test methods to mitigate possible threats include API security testing and functional testing or testing to your security requirements.
Testing your security requirements can start at the software unit verification phase. Next, it moves to the integration verification phase followed by the system verification phase. It may be as simple as utilizing a solution like Parasoft to automate unit testing, integration testing, system testing, and code coverage to ensure test completeness.
Automated test case generation is another powerful capability that cuts effort and cost. In addition, automated reporting and analytics provide actionable feedback to highlight any hot spots and help keep the project on track and in good health.
Step 4: Implementation & Validation
This step ensures that, of the threats addressed, none remain above-accepted levels of risk. In addition, the team should ensure that any risks left fall within accepted parameters, as well.
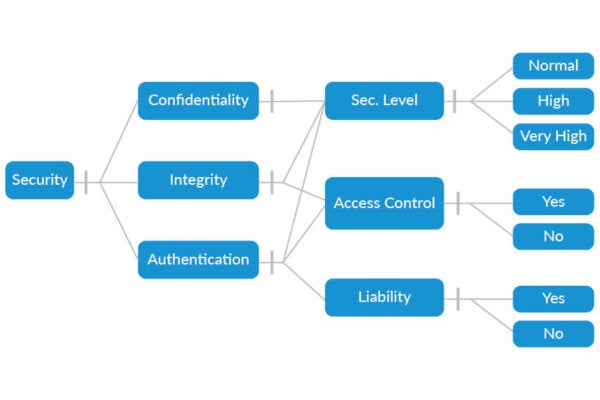
Not every project will require the same method of risk assessment. As such, there are several ways by which teams can measure both the probability and impact of vulnerabilities. One of the most popular options is a threat matrix as seen above—usually in 3×3, 4×4, or 5×5 matrices. Other options include the following:
Decision Tree. This template can help a team visualize different results and the probability of achievement, as well as calculate the potential value of the project, service, or product.
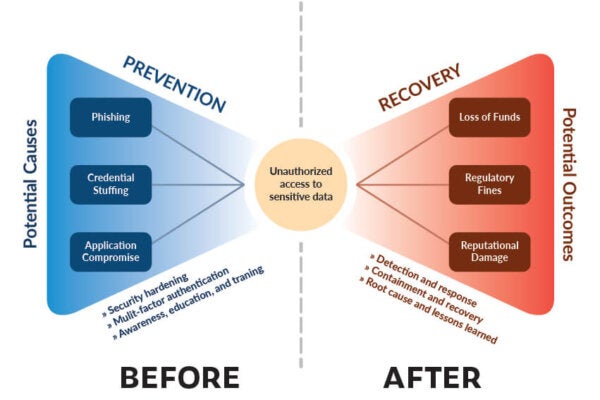
Bowtie Model. This approach displays causal links between threat sources and potential consequences. On the left would be the cause, the center is the inciting event/risk, and the right displays potential outcomes.
Failure mode and effects analysis (FMEA). This analysis, first utilized in the 1940s within the U.S. military, is best for the proposal or design stages of a project. The “failure mode” part defines problems, potential issues, and failures. The “effects analysis” part examines what impact the failures may have.
Determining how best to perform the threat analysis and risk assessment can be somewhat complicated as there are many cybersecurity risk assessment approaches and frameworks that are under deployment. Some come from the government and others come from commercial organizations like NIST, ISO, OCTAVE, NCSA, and so on.
During your process, one of the greatest challenges with threat assessments is identifying all actual potential threats and risk vectors. Baking security processes into development can also represent a significant blocker for some teams. They may not see the value in it or deem the “juice not worth the squeeze” regarding the benefits.
As connected embedded devices, IoT, the cloud, automation, and other technological advancements factor into everyday items like cars and MRI machines, it’s critical to implement and refine strategies around security and risk assessment.
To serve multiple industries and workflows, TARA methods and tools vary in their approaches and advantages. But identifying which tools are best for your project need not be an insurmountable challenge. You can more easily identify the tool you need and the TARA strategy for your team with things like threat matrices.
Many threat matrices capture the set of potential threats and the functions or safeguards that should be put in place. This equates to recognized security requirements and the types of verification and validation (V&V) methods that will need to be employed.
You’ll need a solid requirement management tool like Polarion, Jama, or codebeamer. You can verify and validate these requirements with extensive automated SAST and DAST solutions like Parasoft’s. There are also companies, like itemis, that provide security threat and risk management tools.
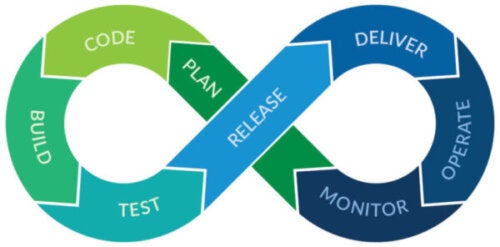
While implementing QA into your CI/CD pipeline is one thing, ensuring security at every leg of automation may be even more critical. When it comes to things like ISO 21434 and ISO 26262 compliance, static analysis security testing (SAST) addresses standards such as CERT, CWE, OWASP, and more. Such as other standards like MISRA, which have incorporated security rules and guidelines into the standard.
Static analysis along with unit testing, compliance reporting, data flow analysis, and other features of Parasoft tools allow your CI/CD pipeline to also automate testing and do more than just shift your development team left. You can augment your already agile SDLC with security-focused and automated processes.
No matter your industry, ensuring safety-critical and security-critical elements are compliant and functioning is development 101. In the same way that a CI/CD pipeline leverages automation for reduced time to market, more effective test results, and better budget use, a TARA can reduce time spent addressing security bugs and threats while also mitigating future problems and identifying any non-compliant assets.
Tests such as static analysis can aid with MISRA compliance whereas Parasoft C/C++test offers a unified software test automation solution that encompasses SAST and DAST testing methods along with support for achieving industry FuSa standards.
“MISRA”, “MISRA C” and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.