See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>


See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>
Jump to Section
Software development includes security as a key component and CERT C++ is one of the best options if you want to follow proper security coding standards. Read on to see why you shouldn't disregard CERT C++.
Jump to Section
Jump to Section
Security is becoming a new mantra of software development teams, especially for those responsible for safety or mission-critical software. In the past, security was often a feature that teams tried to add to already-built systems at the very end of the development cycle, frequently by spinning in vicious circles of pen testing and fixing. Today, we know that security is a solid engineering discipline supported by multiple research programs and standards.
If you want your system to be secure by design, you need to start at the very beginning of the development process and make sure that every line of created code follows security best practices. For teams who develop in C++, one of the best options to rely on is the CERT secure coding standard. Parasoft C/C++test is the only tool that comprehensively supports this standard. Parasoft’s security testing and compliance is the most complete solution on the market for C and C++ code.
The SEI CERT C++ standard, first published in 2006, is an extension of the CERT C standard. Both come from the Computer Emergency Response Team (CERT) of the Software Engineering Institute at Carnegie Mellon University.
The primary goal of CERT C++ is to promote secure coding practices by providing developers with a safer subset of the C++ language that avoids software weaknesses that lead to security vulnerabilities. In addition, these coding rules and practices help improve the reliability and maintainability of the software. The CERT C++ standard is often used as a coding standard to help organizations meet compliance goals for safety and security.
Prior to C++11, the absence or separation of standardization for integer types in C++ caused some developers to use the C language <stdint.h> file for type definitions. This caused compatibility issues in coding, constructing portable programs, and integrating with C++ features. <cstdint> in C++ is a valuable tool because it offers precisely sized integer types, enhancing the portability of the code and decreasing the chances of integer-related security problems. Nonetheless, it’s important to note that merely using <cstdint> doesn’t automatically eliminate vulnerabilities, like integer overflows, type confusion, buffer overflows, format string vulnerabilities, and big/little endian issues that can lead to data interpretation vulnerabilities.
To maintain a secure codebase, you must adhere to established CERT C++ coding best practices, such as thoroughly checking boundaries, choosing the right integer types, and validating input data. These precautions are crucial for reducing the likelihood of security issues.
Primary expressions in C++ are the building blocks of the language and encompass variables, literals, function calls, and so on. In the context of secure coding with CERT C++, primary expressions are a focus since these operations can be potential sources of vulnerabilities. The coding standard provides rules and guidelines for using primary expressions safely, such as:
The SEI CERT C++ standard introduces a collection of rules to enforce secure coding practices and eliminate vulnerable code constructs. The standard is organized into 11 chapters that contain rules in specific topic areas. Unlike CERT C, the CERT C++ coding standard only has rules and no recommendations. They’re pending further review and development.
SEI CERT C++ relies on the CERT C standard and embraces the subset of CERT C rules that apply to C++. At this time—bear in mind that CERT is living standards—there are 143 CERT C++ rules and 136 rules inherited from CERT C. An overview of the CERT C++ standard is presented in the following chart followed by a list of its chapters.
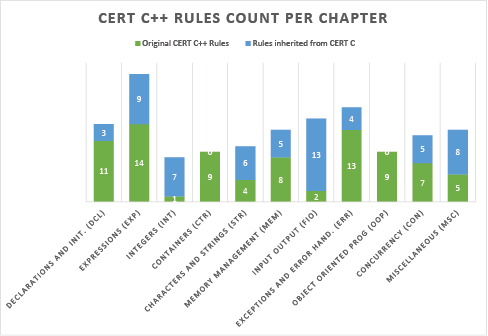
Provides rules and guidelines for declaring and initializing variables and objects in a way that ensures a valid, initialized state and avoids common pitfalls.
Covers rules related to expressions, emphasizing the need for proper handling of expression results, avoiding unintended side effects, and ensuring expressions are well-formed and maintainable.
Focuses on rules for handling integers with an emphasis on preventing integer overflows, underflows, and other issues related to integer operations.
This chapter deals with rules for using C++ standard library containers like vectors and arrays, promoting safe and efficient container management, and usage.
Provides guidelines for proper handling of characters and strings, including ensuring proper null-termination and avoiding common string-related vulnerabilities.
Focuses on rules for effective memory management, including dynamic memory allocation and deallocation, to prevent memory leaks and other memory-related issues.
Covers rules for safe input and output operations, highlighting the importance of validating input data and handling file operations securely.
Addresses rules for managing exceptions and errors, emphasizing best practices for handling exceptions and errors in C++ code.
Provides guidelines for object-oriented programming, including recommendations for class design, inheritance, and polymorphism.
Focuses on rules related to concurrent programming, addressing issues, and best practices for multithreading and parallelism.
Contains miscellaneous rules that don’t fit neatly into the other categories but are important for writing secure and reliable C++ code.
As the chart above illustrates, each of these top-level rules contains more specific rules of which some are specific to C++ and some from CERT C also apply.
Parasoft C/C++test has full support for the CERT C++ coding guidelines. The test configuration (“SEI CERT C++ Rules”) enables all checkers from the original CERT C++ rule set and those from CERT C that are applicable for C++, which is precisely as CERT defines it to assure the security of your C++ codebase. Organizations developing with C and C++, including teams planning to switch to C++, can rely on a single solution with consistent reporting.
Teams also benefit from dedicated compliance reporting for CERT C and C++, for building a sustainable compliance process. With reporting extensions, users can get a dynamic view of the compliance process and review the violations prioritized according to the CERT risk assessment framework.
CERT attributes every violation with scoring for the following three factors:
Priority is computed as a product of these three factors and divided into levels: L1, L2, and L3. L1 represents high-severity violations with high likelihood and low remediation cost. These are the ones that teams are the most interested in fixing, as they indicate serious problems that are not complicated to remediate. Using CERT’s scoring framework provides great help in focusing efforts and enabling teams to make the best use of time budgets.
In addition to widgets, violations explorers, and a risk-scoring framework that helps to quickly orient yourself in the advancement of the compliance process, Parasoft’s reporting framework also saves you time by automatically generating compliance reports that are suitable for code audits. This is an exciting functionality if your organization is more formal with the development process.
C++ is a great language. While it has many features of modern OO language, enabling it to design complex systems with advanced OO design patterns, it also offers great efficiency because it allows you to access memory directly through pointers without checking whether this access is correct.
Of course, these benefits come with a price. With C++, even very experienced software developers can create vulnerable code, most commonly due to memory access and management issues. Buffer overflows, use of dangling references, and integer overflows can all lead to undefined behavior, which can be exploited in multiple ways.
One example is arc injection. An attacker can try to maliciously transfer control to the code existing in process memory other than intended.
Another example is code injection, which is injecting code into the memory of the running system to gain control over a system with privileges of the compromised program, or even worse, with a kernel access level. Once that control is taken, losses can be devastating.
How can we prevent attackers from penetrating our system? It isn’t possible to take an existing codebase and try to guess all possible security breaches. The best option currently available for C/C++ programmers is to create code in the first place that is free from certain constructs that are proven to be a source of security breaches.
Let’s look at a simple illustration. The snippet of source code below is taken directly from the CERT C++ standard (rule EXP61-CPP).
auto g() {
int i = 12;
return [&amp;] {
i = 100; // Problem
return i;
};
}
void f() {
int j = g()();
}
In this example, the function g() returns a lambda, which implicitly captures the automatic local variable “i” by reference. This poorly written code has at least one security vulnerability when lambda is returned from the g() call. The reference it captured will refer to a variable whose lifetime has ended (g function is gone).
As a result, when the lambda is executed in f(), the use of the dangling reference in the lambda affects undefined behavior. This undefined behavior may be exploited to get control over the program. The memory that was occupied by “i” within the lifetime of g function is already freed, and this chunk of the stack is probably already reused for some other purposes, possibly a return address from the function call, which when overwritten can be used to execute arbitrary code.
This specific vulnerability is detectable by the rule, EXP61-CPP A lambda object must not outlive any of its reference captured objects. Source code that’s compliant with CERT C++ should not contain any occurrences of this problem.
CERT C++ includes many more rules that can detect potential problems and will help you promote secure coding practices. Using CERT C++ offers significant benefits to software developers.
Security coding guidelines, when used consistently, can help harden your source code and are the most effective strategy to assure overall system security. These days, it is really difficult to find a justification for not following a security coding standard such as CERT C++.