See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>


See what API testing solution came out on top in the GigaOm Radar Report. Get your free analyst report >>
Jump to Section
With the FDA’s addition of more requirements to their cybersecurity validation and standards comes the need for medical software manufacturers to adopt static analysis to ensure that their software meets these new security standards. Read on to learn how to implement static analysis to meet these security requirements.
Jump to Section
Jump to Section
As the FDA adds more cybersecurity requirements to their software validation guidance, medical device manufacturers can turn to static analysis, the most effective method to address safety and security concerns and deliver predictable software.
Medical device manufacturers continue to focus on improving software development processes for two primary reasons.
The FDA’s new cybersecurity guidance for medical devices was released in September 2023 and provides comprehensive recommendations to the industry regarding cybersecurity device design, labeling, and documentation to be included in premarket submissions for devices with cybersecurity risk.
The guidance is intended to help manufacturers identify and mitigate cybersecurity risks throughout the life cycle of a medical device, from design and development to manufacturing, servicing, and post market surveillance. It also provides recommendations for communicating cybersecurity risks to healthcare providers and patients.
The new guidance builds on the FDA’s previous cybersecurity guidance documents, but it also includes a number of new and updated recommendations, such as:
The FDA used to be focused on functional safety aspects of the systems, but now cybersecurity is a subject of equal importance. Even though safety and security are similar—and you could easily argue that both are about creating predictable software—the FDA considers cybersecurity something that requires dedicated attention and measures.
Process validation is the collection and evaluation of data that establishes scientific evidence that a process is capable of consistently delivering a quality product. In the context of medical devices, process validation is essential for ensuring the safety and effectiveness of devices throughout their life cycle.
Process validation is particularly important for medical devices that are controlled by software, as software can be complex and difficult to test comprehensively. For example, a software-controlled medical device may have millions of lines of code, and it’s not possible to test every possible scenario and combination of inputs and outputs without utilizing both static code analysis and dynamic analysis.
Below are three key reasons why process validation matters.
The regulatory requirements outlined in the FDA guidance document on medical device cybersecurity, are designed to address the growing concerns regarding the security and safety of medical devices in an increasingly connected and digital healthcare environment. Here’s an explanation of the regulatory requirements.
The FDA now has new statutory authority under the Food and Drug Omnibus Reform Act (FDORA), signed into law in December 2022. This law allows the FDA to require cybersecurity information in medical device submissions for “cyber devices” and mandates that manufacturers take specific actions to demonstrate reasonable assurance that their devices and related systems are “cybersecure.” Failure to comply with these requirements is considered a prohibited act, subject to prosecution.
The term “cyber device” is newly defined in the law as a device that includes software validated, installed, or authorized by the sponsor, can connect to the internet, and contains technological characteristics that could be vulnerable to cybersecurity threats. This definition helps clarify which devices are subject to the new cybersecurity requirements.
The new guidance mandates that manufacturers must include specific cybersecurity information in their premarket submissions to the FDA. These premarket submissions can include Premarket Approval (PMA), 510(k), or de novo submissions. The cybersecurity information is required to ensure that the device meets the cybersecurity requirements outlined in the law.
Device manufacturers are required to submit a plan for monitoring, identifying, and addressing post market cybersecurity vulnerabilities and exploits. This plan should outline the manufacturer’s approach to continuously monitoring and addressing cybersecurity risks that may emerge after the device is on the market.
Manufacturers must design, develop, and maintain processes and procedures to provide reasonable assurance that the device and its related systems are “cybersecure.” This requirement emphasizes the need for a proactive approach to building security into the device’s design and maintaining it throughout the device’s life cycle.
Manufacturers are expected to provide a software bill of materials (SBOM) as part of their submissions. This bill should detail the commercial, open-source, and off-the-shelf software components used in the device. This information is crucial for identifying and addressing potential vulnerabilities in the software stack.
The guidance document also empowers the FDA to establish additional requirements through regulations to demonstrate that the device and related systems are cybersecure. Manufacturers must be prepared to comply with any such additional requirements as outlined by the FDA.
A key aspect of the regulatory requirements is the inclusion of a new statutory prohibited act. This means that failure to comply with the FDA’s cybersecurity requirements is not just a compliance issue but also a legal violation. The government has the authority to prosecute violations of these requirements criminally or pursue injunctive relief against noncompliant companies.
Medical device manufacturers must comply with many requirements to ensure the safety, efficacy, and quality of their products. We’ll explore key aspects of compliance with FDA regulatory requirements in medical devices, laying more emphasis on addressing security concerns in medical devices and designing controls and validation protocols for manufacturers.
To comply with FDA regulations and prioritize patient safety, medical device manufacturers must address security concerns effectively. Here are some tips to address security concerns in medical devices:
Proper design controls and validation protocols are vital components of ensuring that medical devices meet FDA regulatory requirements. These controls help manufacturers develop safe and effective devices that deliver the intended benefits to patients.
Here are key considerations for implementing design controls and validation protocols.
Manufacturers can employ various tools and methods to achieve and maintain compliance with FDA regulations for medical devices. Discussed below are essential tools and methods that can aid in the pursuit of FDA compliance.
Static analysis plays a critical role in helping medical device manufacturers meet the stringent requirements set forth by the FDA.
Here are 5 reasons to adopt static analysis for meeting FDA requirements.
Given the place of risk management in achieving the overall objectives or requirements of the FDA, let’s delve into how you can achieve proper risk management.
Many of our medical device customers, when starting from the ground up, have found success introducing static analysis for C/C++ by following these steps:
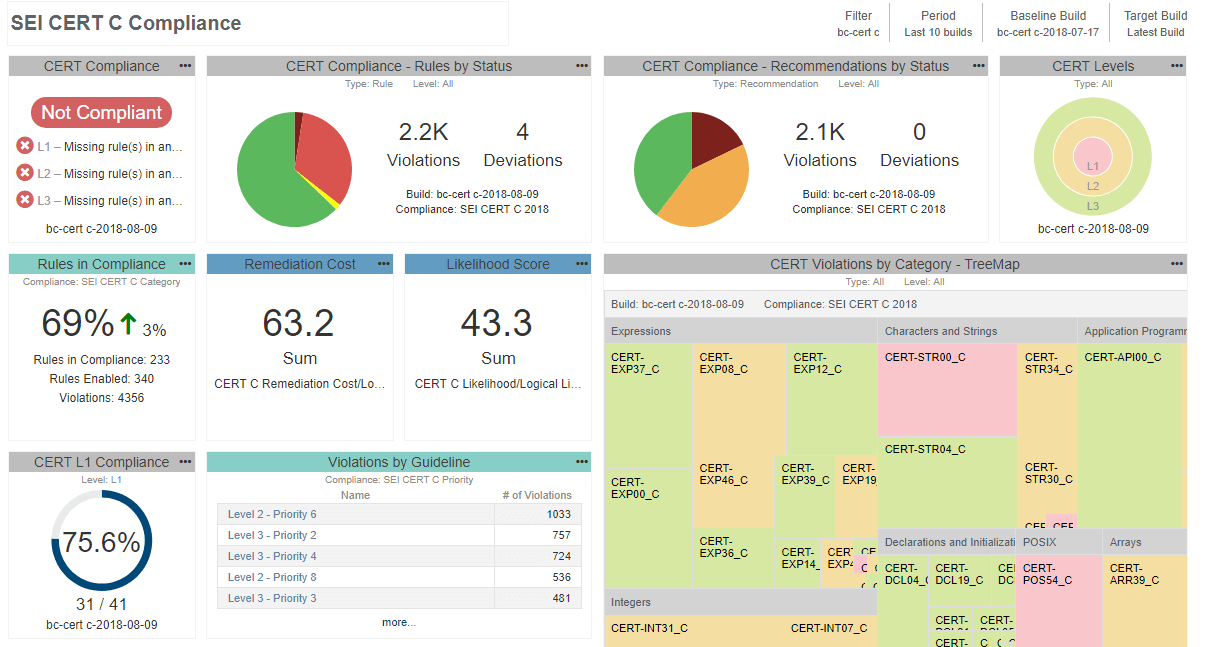
Since static analysis reports become part of the quality management system, you can’t use just any tool. FDA requires that all tools used in development and verification of the software be validated for intended use. There are different ways to demonstrate the tool’s suitability for use in safety-critical development. Depending on the risk of the device, it could be as simple as re-using a certificate of compliance or completing the lengthier process of tool qualification.
For the end user, the most convenient option is to take the credit for the work done by the tool vendor and re-use the certification that is granted for the testing tool by an external certification organization such as TÜV SÜD. Parasoft C/C++test, for example, is covered with a TÜV SÜD certification that can be re-used to demonstrate suitability for developing software according to medical standards like IEC 62304.
For high-risk devices such as Class C, you may need to validate the tool internally in your development environment. The intention is to provide the evidence that the tool operates according to its operational requirements, gathered in the project’s development environment. This is a very tedious and time-consuming process.
The best situation is if your tool vendor can support you in this effort and provide a special tool qualification kit containing well-designed test cases, and the automation framework to execute them in the project’s development environment, and automatically generate the documentation that can serve as the evidence for tool validation. Here again, Parasoft’s flagship product C/C++test, provides an automated tool qualification kit.
We have a plethora of case studies of real-world applications of Parasoft static analysis tools. But let’s look at two distinct success stories that exemplify how our static analysis solution has played a significant role in helping medical device manufacturers overcome their unique challenges and meet FDA requirements.
The following case studies illustrate how Parasoft’s software testing solutions have been instrumental in helping medical device manufacturers address their unique challenges and achieve their goals. Inovytec and Smiths Medical both saw remarkable improvements in code quality, compliance, and testing efficiency through their collaboration with Parasoft.
Inovytec, a company dedicated to producing medical devices, embarked on a mission to achieve FDA 510(k) certification for its Ventway Sparrow ventilator. Their challenge lay in delivering clean code while adhering to FDA regulations. Parasoft’s C/C++ static code analysis solution came to their rescue.
Inovytec’s software development team customized Parasoft C/C++test to align with the stringent FDA requirements. Every time they prepared to release a new software version, they ensured that Parasoft’s static analysis was configured to run according to the FDA regulation definitions. The result was not only improved code quality but also a resounding success in passing 100% of the FDA 510(k) certification rules and guidelines. Parasoft emerged as the preferred testing solution at Inovytec, and their collaboration with ESL, a distributor of Parasoft products in Israel, provided essential support and expertise whenever needed.
Smiths Medical, a renowned manufacturer of specialty medical devices, encountered a series of challenges in its quest to develop high-quality, safety-critical medical device software. Automated testing plays a crucial role in Smiths Medical’s testing strategy.
Past endeavors to incorporate tools fell short of complete success. The development team sought a solution that could enhance their entire testing process by embracing a fresh perspective centered around unit testing and test-driven development (TDD), a methodology that integrates design, testing, and code development. They needed a tool that could fit within their testing pipeline and enhance their overall development culture. Parasoft C/C++test proved to be the answer to their challenges.
The software team not only achieved successful TDD adoption but also benefited from improved test stability, enhanced code coverage, and a streamlined tool qualification process, which was critical for safety-critical applications. With Parasoft, Smiths Medical was able to transform its development processes, making testing an integral part of its software pipeline, and ultimately, ensuring the delivery of safe, high-quality medical devices.
The FDA validation process can be complex and challenging for medical device manufacturers. However, there are a number of steps that manufacturers can take to overcome these challenges.
The FDA provides essential validation guidance for medical device manufacturers to ensure product quality and patient safety. As regulations and guidelines evolve, staying on top of these changes and planning for future compliance is crucial. Two ways medical device manufacturers can do this is to prepare for future FDA guidelines and remain compliant.
The FDA is constantly updating and revising its guidance documents for medical device manufacturers. To prepare for future FDA guidelines, medical device manufacturers should:
Medical device manufacturers must ensure continuous compliance with FDA regulations. To do this, manufacturers should:
Over time, achieving FDA compliance has proven to be quite rigorous and time-consuming. However, with static analysis and dynamic analysis tools, these challenges can be overcome. Static analysis tools offer advanced static code analysis capabilities, which help identify and rectify issues in software and code early in the development process.
Introducing static analysis is a dedicated effort, requiring developer time and cost. But it’s a proven way to harden your system against malicious attacks. Deploying static analysis with a well-thought-out set of security guidelines enables you to build systems that can stand up against unforeseen future attacks.
“MISRA”, “MISRA C” and the triangle logo are registered trademarks of The MISRA Consortium Limited. ©The MISRA Consortium Limited, 2021. All rights reserved.